Okta is enterprise-grade software that is merely built for cloud applications. But its usage isn’t restricted to it, as many on-premises applications show compatibility with Okta. Managing user’s access to multiple devices and applications is now possible with the help of this enterprise-grade. In this technological world, everything has advanced so much that it is impossible to keep a track record. With advancement comes challenges like identity issues, employee mobility, security concerns, etc. Well, there is one solution to all these problems: Okta.
Features
Although there are numerous features of Okta but the most prominent ones are:
- Provisioning
- Single Sign-On
- Active Directory
- Multifactor Authentication
Okta Integration Network (OIN) is a pre-integrated network of applications. The most crucial role of this network is that it brings together all the features of Okta. Okta and IAM Identity Center go together. IAM Identity is a literal center that assists in managing single sign-on access to cloud applications and your AWS accounts. Moreover, it supports synchronization. It is the process of provisioning information from Okta to the Identity Center with the help of the SCIM 2.0 protocol.
Benefits of integrating Okta with AWS for user and access management
Before jumping on to the “How” part, we would like to discuss about the benefits that you will get after integrating Okta with AWS.
- A single click is required by the users to perform a sign-in to IAM Identity Center
- It provides mapping of authorized users to their relevant AWS resources and accounts
- The groups having memberships in Okta will have their memberships moved to IAM Identity Center as well
- Developers will have two options for their sign-in; with Okta credentials or with Okta Multi-factor Authentication
What is SSO (Single Sign On)?
After having a pretty good view at the introductory part, now is the time to get familiar with some basic terminologies. Let’s take a start from SSO.
The full form of SSO is Single Sign On. Meaning of this term is pretty self-explanatory but we will still explain it to you. So basically when a user uses a single set of sign-in credentials for accessing multiple applications then it can be called as SSO.
Importance of integrating identity management in cloud environments
Where cloud environments are super secure, they are also prone to many attacks. The priority should be to provide as much security to these environments as possible because one cannot afford to risk it at all.
One way is to integrate the identity management in cloud environments. There are numerous advantages of it, if you want to know a few of them then visit the below section.
- Connections of users is secure on the cloud as well as on-premises
- A consistent and stable access control interface is provided to the users
- High security layers and levels are offered
- Many businesses can access resources at fairly diverse level
Prerequisites
- You must own a developer’s account or a licensed Okta account
- You must have administrative authority for managing permissions and users in Okta
- An up and running AWS account
- An administrative access to IAM Identity Center
Architecture
Integration Steps
There are two approaches to integrate Okta with AWS IAM Identity Center; CLI and console based. We will be discussing both of them down below.
CLI Approach
One thing to remember regarding this approach is that the overall integration procedure cannot be done by only using the CLI commands. There have to be certain configurations that need to be made in the web consoles of Okta and AWS.
AWS CLI Commands
First we will deal with the AWS CLI commands.
- Installing AWS CLI
You need to have AWS CLI version 2 installed as it shows compatibility with AWS SSO.
For Linux
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
unzip awscliv2.zip
sudo ./aws/installFor Windows
You have to install AWS CLI from here.
- Configuring AWS CLI
You need to configure AWS CLI in order to use AWS SSO for the purpose of authentication
aws configure sso- Signing-in using AWS SSO
Use the following command to perform a login
aws sso loginA new browser window will be opened for the completion of login process
Okta CLI Commands
Although AWS CLI commands are limited in scope but Okta CLI commands win this competition here.
- Installing Okta CLI
The installation of Okta is different for every operating system that is why it is a good approach to visit its official documentation for this cause.
For Windows
choco install oktaFor Linux
-# Add Flathub repo
flatpak remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepo
# install the package
flatpak install flathub com.okta.developer.CLI
# add this to your appropriate dot file
alias okta="flatpak run com.okta.developer.CLI"
curl https://raw.githubusercontent.com/okta/okta-cli/master/cli/src/main/scripts/install.sh | bash- Configuring Okta CLI
The next step is to configure your Okta CLI with the API token and Okta domain.
okta loginAdditional Web Configurations
The web configurations that need to be performed additionally are mentioned below.
- You need to create an SAML 2.0 protocol application in Okta
- Importing SAML metadata in IAM Identity Center being exported from Okta
- Finally mapping Okta groups to the AWS roles
- Create a SAML 2.0 type Okta application and configure it with respect to AWS IAM Identity Center
- Note down the issuer URL and x509 certificate information of Okta application
- Now configure AWS IAM Identity Center in such a way that it works as an identity provider in Okta application
- Use the following command to create an identity provider corresponding to your Okta application in IAM Identity enter
aws iam create-identity-provider
aws iam create-identity-provider --name okta --type SAML --attribute-mapping file://mapping.json --metadata file://metadata.xmlUse aws iam enable-identity-provider-for-user command in order to enable the identity provider for users
aws iam enable-identity-provider-for-user --user-name user1 --identity-provider-id oktaNow assign groups and users to the AWS IAM Identity Center application in Okta from Okta. This will perform the perfect synchronization of users between IAM Identity Center and Okta.
Console Approach
Now let’s take things to a console based level, which is already available in documentation. From setting up an Okta account to all of its advanced configurations, we will discuss everything.
Connect Okta with IAM Identity Center
- Perform a sign in to the AWS Management Console
- Open the console of IAM Identity Center
- Choose “Settings” option from the navigation pane
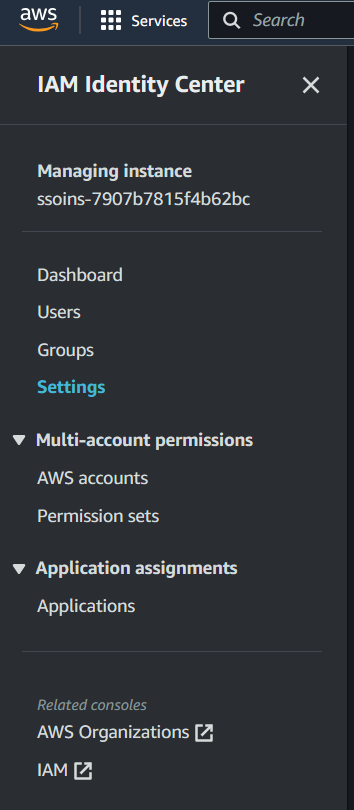
- As soon as you are directed to the Settings page, choose Identity Source tab
- Choose Change Identity Source from the Actions menu
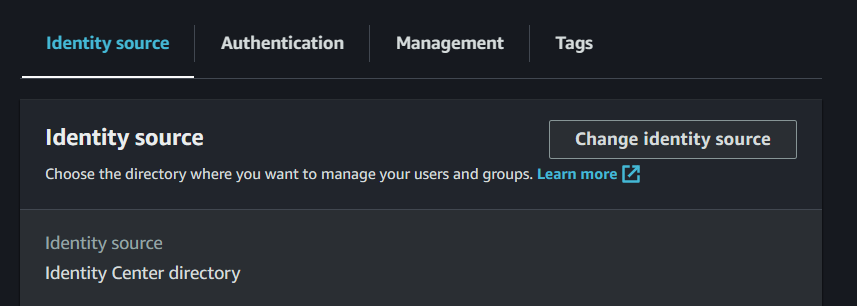
- Now choose External Identity Provider and click Next
- Just below Service Provider Metadata, make sure to check the following values
- IAM Identity Center Assertion Consumer Service (ACS) URL
- IAM Identity Center issuer URL
NOTE: Make sure to stay on the same page.
Create an IAM Identity Center Okta Application
- Open a new tab and perform a sign in to Okta console
- Select Applications from the navigation pane
- You will be directed to the Applications page. Click on Browse App Catalog
- Now search for AWS IAM Identity Center and choose Add Integration
- Select Done
Configure the IAM Identity Center Application in Okta
- Find and select Sign-on tab in the Okta console
- Select “Edit” to edit the SAML settings
- Now copy and paste IAM Identity Center ACS URL and IAM Identity Center issuer URL under the Advanced Sign-on Settings
- Click on Save
Upload SAML metadata from Okta to IAM Identity Center
- Click on the Sign-on tab present in the Okta console
- Choose Action under the SAML signing certificates and then select View Idp Metadata
- Save the file with the following extension: idp-saml.xml
- Select Next, review the required changes and then confirm them
Enable SCIM to synchronize users and groups
- Choose Settings from the navigation pane of IAM Identity Center Console
- Search for Automatic Provisioning and then select Enable under it
- To access token to a text-editor copy the SCIM endpoints
Create SCIM application to push users and groups to IAM Identity Center
- Click on Browse App Catalog present on the Application page of the Okta console
- This time search for SCIM 2.0 test app and choose Add integration option
- Navigate to the General Settings page and do the following:
Enter SCIM 2.0 TestApp in the Application Label
- Check the options saying: Do not display application icon to users and Do not display application icon in the Okta Mobile App
- Select Next and then choose Done
- Select Configure API Integration under the Provisioning Tab
- Choose the option Enable API Integration
- Enter the SCIM endpoint for SCIM 2.0 Base URL
- Select Save and then Edit
- Choose the option Enable Create Users and then select Save
Create a rule that pushes users and groups to IAM Identity Center
- Search for Push Groups tab in the Okta console
- Select Find Groups by Rule
- Name the rule as AWS SSO Rule
- Use awssso as the prefix
- Choose Immediately push groups found by this rule and then select Create Rule
- Go to the navigation pane and choose Directory. After this select Groups
- Choose Add Group and fill the field with the following information:
Name: AWS Users
- Select “Save”
- Now select AWS Users Group on the Groups page
- Choose Assign Applications on the Applications Tab
- Select AWS IAM Identity Center Application and then select Assign
- Choose Assign for the SCIM 2.0 Test App and select Save
- Choose Done
Create a New Group in Okta
- Choose Directory and then Groups from the navigation pane present on the Okta Console
- Choose Add Groups and enter awsssoPowerUsers in the name field and select Save
- Choose Applications from the top navigation menu
- Open the SCIM 2.0 Test App application
- Select Push Groups
- Notice that awssoPowerUsers is being listed and marked as Active
- In the IAM Identity Center console, choose Groups from the navigation pane and see awsssoPowerUsers is being listed with no users
Assign a Permission Set in IAM Identity Center
- In the navigation pane of IAM Identity Console, select AWS accounts and choose your organization
- Select all the accounts in the organization
- Now choose Assign users or groups and then select Groups
- Select awsssoPowerUsers
- Select “Next”
- Choose AWSPowerUsersAcces
- Select Finish
- Choose Proceed to AWS Accounts
Create a User in the Okta Portal
- From the top navigation bar in Okta console, choose Directory and then People
- Select Add Person
- On the relevant page, add the following information:
- Choose User for User Type
- Enter User’s First Name for First Name
- Enter User’s Last Name for Last Name
- Enter User’s email address for User Name
- Enter User’s email address for Primary email
- Enter awssoPowerUsers and AWS Users for Groups
- Choose set by admin and then enter password for Password
- Uncheck User must change password on first login and then select Save
- Now navigate to IAM Identity Center console
- In the navigation pane choose Users and you will see the users created in the list
- Open General Information by choosing the User Name
- Make the confirmation that the user appears as CreatedBy:SCIM
Verify the New User is Authenticated and has Access
- Open dashboard from the navigation pane of IAM Identity Console
- Copy the User Portal URL
- Make sure to open a new tab in a private mode
- Paste the copied URL in the address bar and you should be redirected to the Okta login page
- Fill in the required credential
- You should be logged in successfully
Verify the New User has Access to AWS account
- Choose AWS accounts in the IAM Identity Center Console
- Choose your organization’s management account
- Choose management console on the AWSPowerUserAccess
- Make sure the AWS Management Console launches
So the process ends here, hope you had a great time reading this.
Conclusion
The future of AWS IAM Identity Center and Okta is very vast. They hold great importance individually and on combined level as well. Advanced security layers and levels will be provided for managing the AWS accounts, resources and cloud environments. What else would a person want? Make sure to get the best out of it.