


SUDO Consultants, the leading AWS Premier Tier Services Partner in UAE and KSA, helps businesses digitally transform their operations with the power of the cloud. We help you leverage the full potential of the cloud to streamline and automate your business processes, reduce operational costs, and gain a competitive edge.
SUDO Consultants, headquartered in Dubai and operating a regional office in Riyadh, supports clients across the US, Asia Pacific, Europe, the Middle East, and Africa. As an AWS Premier Tier Partner, we help you build, migrate, and manage applications on AWS. We also enable data driven decision making by integrating advanced data platforms, analytics, and AI solutions on AWS.
Our experienced team is here to help you get the most out of your cloud investment. Get started today!
SUDO Consultants the leading AWS partner in UAE helps businesses to digitally transform their operations with the power of the cloud. We help you leverage the full potential of the cloud to streamline and automate your business processes, reduce operational costs and gain a competitive edge. SUDO Consultants, headquartered in Dubai, provides services to a wide range of clients across the US, Asia Pacific, Europe, the Middle East and Africa. We provide cloud consulting services that help you build, migrate, and manage applications on the AWS platform. Our experienced team is here to help you get the most out of your cloud investment. Get started today!
As an AWS Premier Tier Services Partner, SUDO Consultants is among the top 1% of AWS partners globally, recognized for proven customer success, deep cloud expertise, and technical excellence.
We specialize in helping organizations across the Middle East migrate, modernize, and secure their infrastructure on AWS, while enabling innovation through DevOps, cloud-native apps, and Gen AI and Agentic AI solutions.
Our certified AWS experts design, implement, and manage secure, scalable cloud environments, with full focus on your business outcomes, cost efficiency, and speed-to-market.
Leverage innovation and maximize outcomes from applications, cloud, workplace, analytics and hyperscale computing

Using the AWS Well-Architected Framework we identify areas of improvement within your chosen AWS environment.

At SUDO, we understand your business model at the moment, but more importantly, we are able to realize where you are going.

Don’t have enough space to keep up with Data Surge? Interested in adoption of Public Cloud? Is OPEX cost becoming a concern.
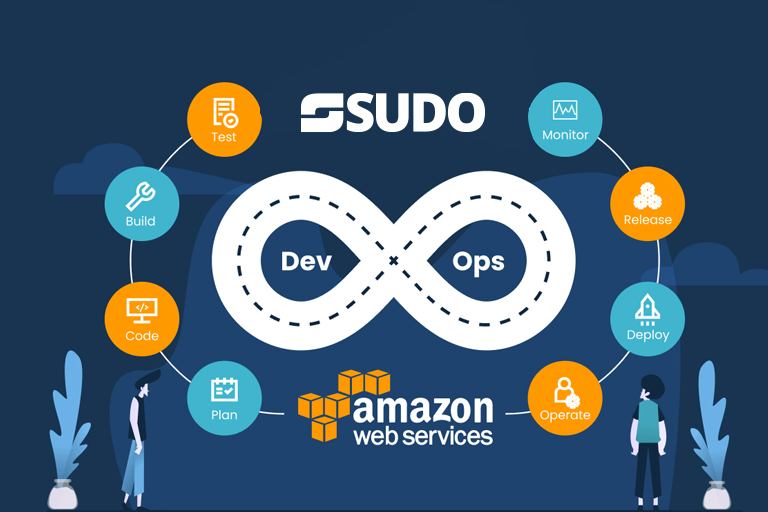
Achieve exceptional results by consulting a certified DevOps Professional. Conventional ways of marketing are outdated.

Our Cloud Management Services engages our clients to construct a custom arrangement that satisfies their novel prerequisites...
Bring the power of AI to your business in a way that feels seamless and transformative.
Our services is only as successful as the technology, innovation and hard work of our experienced staff. To access our services quickly, we’ve organized 3 easy steps to make it happen!

Our solutions are specially tailored around your business’s pain points. In depth call meetings

We provide exceptional digital solutions, ensure on-time delivery and guarantee results

Our team offers 24/7 customer support via our official channels - so you're always covered!















They have been quite friendly and supportive thought our entire experience so far. Specially a well experienced team with solid knowledge of the domain.
Sudo team was very customer-centric and willing to go the extra mile to ensure that the project was delivered on time. They took on more work where needed at no extra cost to Accelerex, and they were able to help mentor our team members. Sudo was an excellent choice for us and I would recommend them.
Highly skilled and professionals. Reliable in any situation. They know very well AWS solutions and know how to implement, findining out of the box solutions.

SUDO consultants are honest, communicative, and hard-working technicians, that have extensive hands-on AWS experience. Their work is impeccable, they are super fun to work with and they are very fairly priced.

The team is extremely talented. They actively listen and design first-class systems all while communicating in almost real-time to questions, concerns, or comments. On this specific project, we used them for they were provided the problem and took in our requirements, and offered a solution that not only was what we expected but better saved us resources run time, and costs. I highly recommend using SUDO for any AWS dev-ops or mirco-services projects.

I am very glad to have done this review with SUDO Consultants. From the very start, SUDO Consultants were very helpful and supportive. The team has a lot of experience with modern architectures and workflows. They have helped us modernize the application and improve our security practices.

Quick response to support request. Excellent knowledge of the product. Great communications and updates

Build the Digital Enterprise of Tomorrow with Cloud Transformation
Achieve sustainable growth and stay ahead of your competition.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |