A web application firewall (WAF) is an important security tool that protects your web applications by acting as a gatekeeper. It sits in front of your web application, analyzing each incoming request and making sure it doesn’t contain any malicious intent. Think of it as a bouncer for your website, checking for any suspicious activity and blocking it before it reaches your valuable information.
Why use a web application firewall? (WAF)
With a WAF, you can protect your web applications from a wide range of attacks, including; SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). These are all common methods used by cybercriminals to steal sensitive data or take control of your website. The WAF checks for any signs of these malicious attempts, and blocks them before they can cause damage.
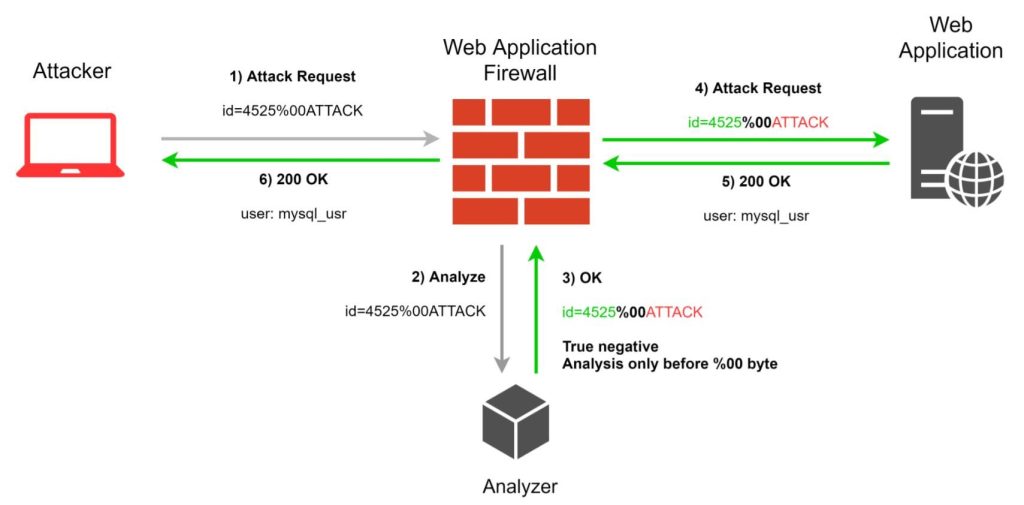
In addition to blocking known attacks, WAFs also come with other useful features. Some WAFs include IP blocking, which prevents traffic from specific IP addresses from reaching your web application. This can be useful if you’re experiencing a DDoS attack or want to block malicious IPs.
Other WAFs come with rate limiting, which is a way to control the rate at which a user can make requests. This can be useful to prevent brute force attacks. Many WAFs also have bot detection feature which can detect malicious bots and block them from accessing your web application
WAF can be implemented in hardware or software, and can be deployed on-premises or in the cloud. Some popular WAFs include F5 BIG-IP, Imperva Incapsula, and AWS WAF. Some web server software and hosting services also come with built-in WAFs.
WAFs can be useful for protecting web applications against a wide range of attacks, including those targeting known vulnerabilities for which there may not yet be a patch available.
It’s worth noting that WAF isn’t a silver bullet and alone cannot protect your application from all types of attack, a comprehensive security strategy should also include other layers of security such as input validation, security headers, access control and encryption.
AWS Web Application Firewall (WAF)
AWS Web Application Firewall (WAF) is a powerful security service offered by Amazon Web Services (AWS) that helps protect your web applications from a wide range of common exploits that can negatively impact availability, compromise security, or consume excessive resources.
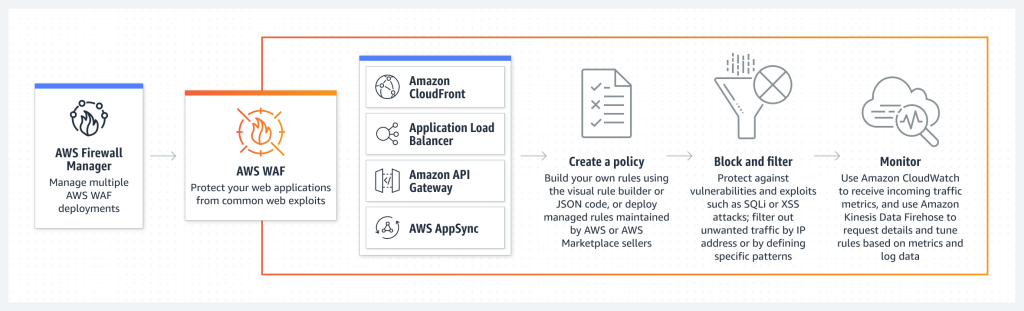
Some features of AWS WAF include:
- Rule groups: You can use pre-defined rule groups to block common web exploit attempts, such as SQL injection and cross-site scripting (XSS) attacks.
- Custom rules: You can also create your own custom rules to block specific strings or patterns that you choose.
- Real-time metrics: AWS WAF provides real-time metrics and logs to help you understand which requests are being blocked and why.
- Integration with other AWS services: AWS WAF can be integrated with other AWS services, such as Amazon CloudFront and Application Load Balancer (ALB), to provide additional protection for your web applications.
Beyond its functionality, AWS WAF is also cost-effective, with pricing based on the number of web requests, the number of web access control lists (ACLs), and the number of rules used. This makes it accessible to businesses of all sizes.
In addition to that, AWS WAF also integrates with other security services like Amazon GuardDuty, AWS Security Hub, and Amazon Macie to give a more comprehensive security protection to your application and allow you to spot any potential threats to your application.
Conclusion
AWS Web Application Firewall (WAF) offers a robust solution for safeguarding web applications against common exploits and threats. The service features a variety of powerful tools, such as pre-defined rule groups and the ability to create custom rules, real-time metrics and logs, and seamless integration with other AWS services. This makes it a comprehensive solution for protecting web applications and their underlying infrastructure.