In today’s interconnected world, the security and privacy of your data are paramount. AWS PrivateLink offers a solution to securely access AWS services without traversing the public internet. By implementing PrivateLink, you can ensure data privacy and compliance while maintaining the benefits of AWS services. In this blog post, we will explain how to use AWS PrivateLink for secure access.
What is AWS PrivateLink?
AWS PrivateLink is a service that allows you to access AWS services securely without going over the public internet. Instead, it leverages Amazon’s private network infrastructure, providing a dedicated and private connection to AWS services. This offers several advantages, including improved security, reduced latency, and compliance with data protection regulations.
Implementing AWS PrivateLink
To implement AWS PrivateLink for secure access, follow these steps:
1. Create a VPC:
To create a VPC, navigate to the VPC Dashboard in the AWS Management Console. Click on “Start VPC Wizard” and select “VPC with a Single Public Subnet.” Fill in the necessary details and create the VPC.
aws ec2 create-vpc --cidr-block 10.0.0.0/16 2. Enable DNS Resolution and DNS Hostnames:
Once the VPC is created, select your VPC from the VPC Dashboard. In the Actions menu, click on “Edit DNS Resolution” and “Edit DNS Hostnames”, set them to Enabled.
aws ec2 modify-vpc-attribute --vpc-id <your-vpc-id> --enable-dns-support aws ec2 modify-vpc-attribute --vpc-id <your-vpc-id> --enable-dns-hostnames 3. Create an Interface VPC Endpoint:
Navigate to the Endpoints section on the VPC Dashboard and click “Create Endpoint.” Select the service name for the AWS service you want to access privately, for example, com.amazonaws.us-east-1.s3. Ensure to select “Interface” as the VPC endpoint type.
aws ec2 create-vpc-endpoint --vpc-id <your-vpc-id> --service-name com.amazonaws.us-east-1.s3 --vpc-endpoint-type Interface 4. Configure Route Tables:
Now, navigate to the Route Tables section on the VPC Dashboard. Select your route table and click on the Routes tab. Click “Edit routes” and “Add route.” Input the destination as the AWS service endpoint and the target as the VPC endpoint ID.
aws ec2 create-route --route-table-id <your-route-table-id> --destination-cidr-block 10.0.0.0/16 --vpc-peering-connection-id <your-vpc-endpoint-id> 5. Test the PrivateLink Connection:
With everything set up, you can now test the PrivateLink connection using the AWS CLI. For example, if you created an S3 endpoint, use the following command to list the buckets in your S3.
aws s3 ls --endpoint-url https://s3.us-east-1.amazonaws.com In the above steps, replace <your-vpc-id>, <your-route-table-id>, and <your-vpc-endpoint-id> with your actual VPC ID, route table ID, and VPC endpoint ID, respectively.
Note: The AWS CLI commands are provided to allow you to set up and verify the PrivateLink connection from the command line if desired, or you can use the AWS Management Console for a GUI-based setup. Each step is crucial to ensuring a secure, private connection to AWS services without traversing the public internet.
Benefits of AWS PrivateLink
- Enhanced Security: PrivateLink ensures that your data never leaves the AWS network, reducing exposure to potential security threats.
- Data Privacy: PrivateLink keeps your data private and prevents exposure to the public internet, safeguarding sensitive information.
- Low Latency: By utilizing AWS’s private network, PrivateLink reduces latency, ensuring fast and efficient data transfers.
- Compliance: PrivateLink helps you meet compliance requirements, especially for regulations that mandate data isolation and privacy.
Conclusion
AWS PrivateLink is a valuable tool for securely accessing AWS services without relying on the public internet. By following these steps, you can enhance the security and privacy of your data while ensuring compliance with relevant regulations. Make use of PrivateLink in your AWS infrastructure to take advantage of its numerous benefits.
For visual reference, illustrating the PrivateLink architecture:
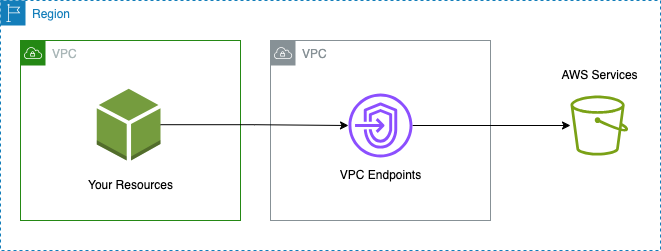
By following this guide, you can securely access AWS services through AWS PrivateLink, ensuring data privacy and compliance with ease. We hope you found this guide helpful in implementing AWS PrivateLink for secure access. If you have any questions or need further assistance, please feel free to reach out.