Introduction
In this article we will be learning how we can access our AWS EC2 instances with the help of AWS System Manager, eliminating the need of SSH keys. Security is a paramount concern, and best practices dictate keeping our applications private. Developers and administrators often need to connect to EC2 Instances for their tasks. However, if these instances are private, accessing them requires additional tools like a bastion or a VPN, leading to increased costs and management complexities. Session Manager (formerly SSM Systems Manager) addresses this issue by offering secure, private SSH access, eliminating the need for costly and complex solutions.
Session Manager enables you to oversee and govern your EC2 instances through a simple browser-based shell with just a click, eliminating the need for AWS CLI, Bastion hosts, Jump hosts, or SSH keys. This offers a straightforward and highly secure method for accessing your AWS EC2 instances.
To utilize Session Manager, it’s essential to have an SSM agent installed on the specific EC2 instance. If the chosen AMI already includes an SSM agent by default, ensure that it is not only installed but also enabled and running properly.

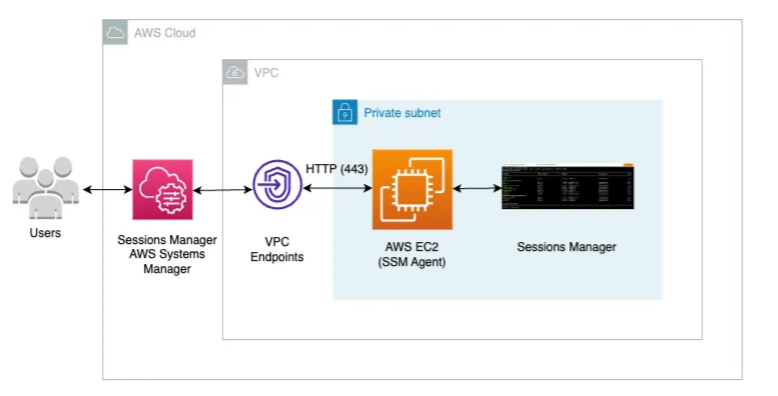
Infrastructure Diagram
Amazon Machine Images with Pre-installed SSM agent
The below-specified AMIs come pre-installed with the SSM agent:
- Amazon Linux Base AMIs dated 2017.09 and later
- Amazon Linux 2
- Amazon Linux 2 ECS-Optimized Base AMIs
- Amazon Linux 2023 (AL2023)
- Amazon EKS-Optimized Amazon Linux AMIs
- macOS 10.14.x (Mojave), 10.15.x (Catalina), and 11.x (Big Sur)
- SUSE Linux Enterprise Server (SLES) 12 and 15
- Ubuntu Server 16.04, 18.04, and 20.04
- Windows Server 2008–2012 R2 AMIs published in November 2016 or later.
- Windows Server 2016, 2019, and 2022.
Advantages
- Session Manager substitutes SSH for our EC2 instances.
- It is applicable to both EC2 instances and On-Premises environments.
- Apart from replacing SSH for EC2 instances, it enables specific actions on groups of instances, such as patching, automation, compliance enforcement, and monitoring.
- There’s no need for additional ports to access the CLI, enhancing the security of connecting to our instances.
- It logs session activities and commands, offering comprehensive audit trails for compliance adherence and troubleshooting needs.
Approach
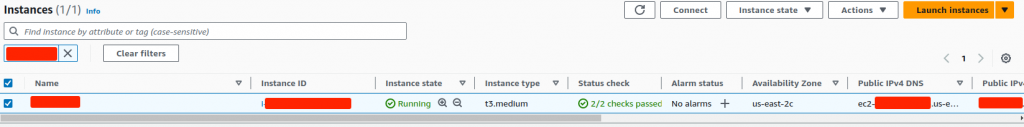
- Launch a private AWS EC2 instance.
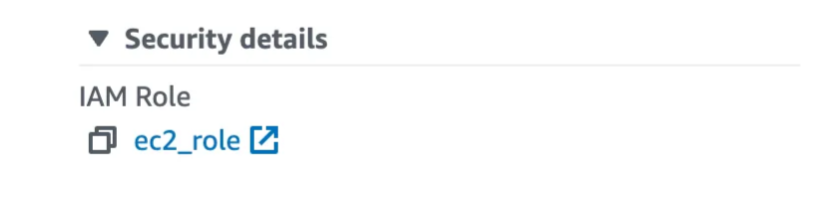
- Create an Instance profile with
AmazonSSMManagedInstanceCorepolicy for the private instance.

- Create three interface endpoints:
ssm,ssmmessagesandec2messages.
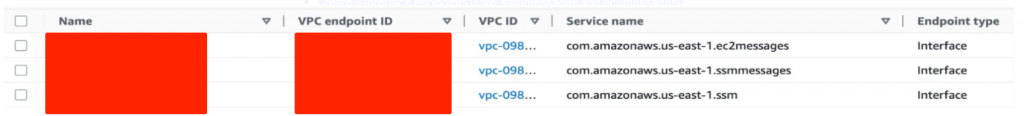
- When setting up Endpoints, choose the private subnets located within the same availability zone as the EC2 instance. For enhanced high availability, it’s possible to select multiple availability zones as well.
- Security group inbound rule of endpoints:
| IP version | Type | Protocol | Port range | Source | Description |
| IPv4 | HTTPS | TCP | 443 | 1.10.0.0/22 | TLS from VPC |
Connecting to private EC2 instance via Session manager
- Choose the instance.
- Click on
Connect. - Go to
Session Managertab.
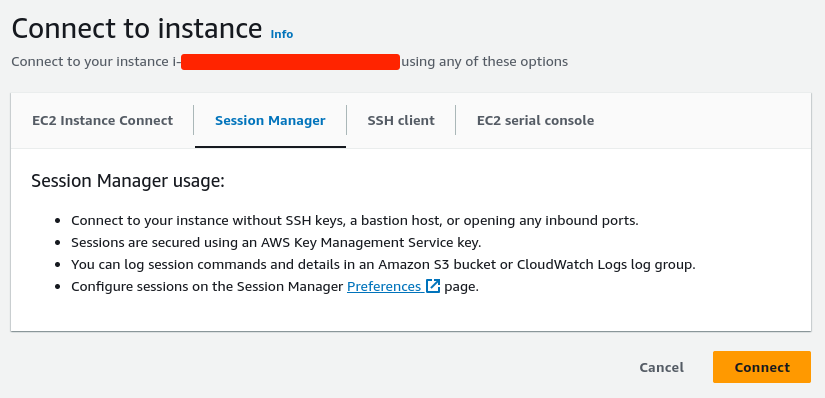
- Click on
Connectto connect via Session Manager.

Conclusion
In conclusion, utilizing AWS Session Manager to connect to private EC2 instances offers a streamlined, secure, and efficient solution for managing remote access. By eliminating the need for SSH keys, bastion hosts, or VPNs, Session Manager simplifies the access process while enhancing security. Its ability to work seamlessly with private subnets and across multiple availability zones ensures high availability and reliability. Moreover, Session Manager provides detailed audit trails, enabling robust compliance monitoring and troubleshooting capabilities. This service not only simplifies the management of remote connections but also strengthens the overall security posture of AWS environments, making it a valuable tool for organizations seeking efficient and secure access to their private EC2 instances.