Introduction
Continuous Integration and Continuous Deployment (CI/CD) are critical practices in contemporary software program development, ensuring fast and reliable shipping of software. When it comes to infrastructure as code (IaC), those practices can drastically streamline the deployment system. GitLab CI/CD offers a comprehensive solution for automating infrastructure deployment. In this manual, we’re going to use Terraform to provision resources on AWS and integrate this technique right into a GitLab CI/CD pipeline.
Prerequisites
GitLab Account: Ensure you have a GitLab account, and a project set up.
AWS Account: You’ll want get access to an AWS account for deploying infrastructure.
Terraform: Basic knowledge of Terraform and its configuration files.
Git: Familiarity with Git for version control.
Setting Up the GitLab Repository
First, create a new repository on GitLab. This repository will store your Terraform configuration files and the GitLab CI/CD pipeline configuration.
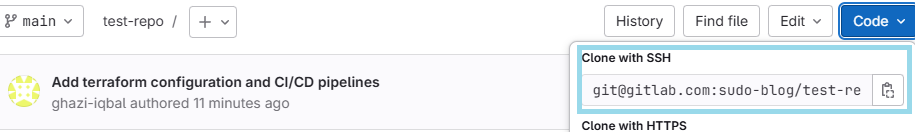
Copy the Clone with SSH
# Clone the new repository locally
git clone https://gitlab.com/your-username/your-repo.git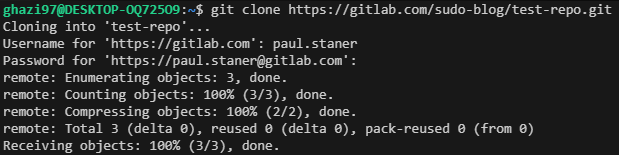
cd your-repo 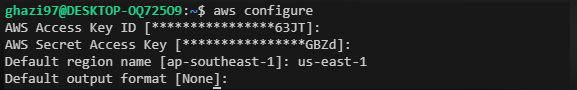
# Create the necessary directory structure
mkdir -p infrastructure/terraform
# Creat the necessary file for gitlab CI/CD:
Vi -p .gitlab-ci.yml
Writing the CI/CD Pipeline
The .Gitlab-ci.Yml file is essential for defining the CI/CD pipeline. Below is an example configuration for deploying infrastructure the usage of Terraform.
yaml
Code:
stages:
- init
- plan
- apply
variables:
TF_ROOT: "infrastructure/terraform" # Directory where your Terraform code is stored
TF_VAR_aws_access_key: $AWS_ACCESS_KEY_ID
TF_VAR_aws_secret_key: $AWS_SECRET_ACCESS_KEY
before_script:
- apt-get update && apt-get install -y curl unzip python3-pip jq
- pip3 install awscli
- curl -LO https://releases.hashicorp.com/terraform/1.9.3/terraform_1.9.3_linux_amd64.zip
- unzip terraform_1.9.3_linux_amd64.zip
- mv terraform /usr/local/bin/
- terraform --version
default:
image:
name: ubuntu:20.04
entrypoint: [""]
init:
stage: init
script:
- echo "Listing repository contents:"
- ls -la
- echo "Listing contents of $TF_ROOT:"
- cd $TF_ROOT
- ls -la # List files in the Terraform directory
- terraform init
plan:
stage: plan
script:
- cd $TF_ROOT
- terraform init
- terraform plan -out=tfplan
apply:
stage: apply
script:
- cd $TF_ROOT
- terraform init
- terraform apply -auto-approve tfplan
when: manual
Configuring Infrastructure as Code
Within the infrastructure/terraform directory, create your Terraform configuration files. For example, to create an default vpc and S3 bucket :
Create Terraform configuration files:
Inside the infrastructure/terraform directory, create a file named main.tf with the
HCL
Code:
#As a sample:
provider "aws" {
region = "us-east-1"
}
resource "aws_vpc" "main" {
cidr_block = "10.0.0.0/16"
instance_tenancy = "default"
}
resource "aws_s3_bucket" "SUDO1" {
bucket = "my-tf-test-bucket97"
tags = {
Name = "My bucket"
Environment = "Dev"
}
}Integrating with AWS
To integrate AWS with GitLab CI/CD, you’ll need to configure AWS credentials in your GitLab project. Go to your project settings and navigate to CI/CD > Variables. Add the following variables:
AWS_ACCESS_KEY_ID
AWS_SECRET_ACCESS_KEY
These variables will be used by Terraform to authenticate with AWS.
Running the Pipeline
Once the whole thing is installation, commit your changes and push them to the GitLab repository. This action will cause the CI/CD pipeline.
Command:
git add .
git commit -m "Add Terraform configuration and CI/CD pipeline"
git push origin main

After pushing the repository, go to GitLab to monitor the pipeline stages.
Stages1 Running

Stage2 Pass 
After moving to the third stage in the pipeline, we must run it manually because we set up the CI/CD configuration to be manual. If we change it to automatic, it will run automatically and pass the third stage.
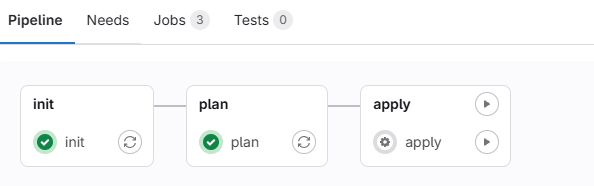
Monitor the pipeline execution inside the GitLab CI/CD interface. If any troubles arise, the logs will help you troubleshoot and fix them.
Best Practices
Security: Use GitLab CI/CD variables to securely store sensitive information such as AWS credentials.
Modularity: Organize your Terraform code into modules to improve reusability and maintainability.
Testing: Implement automated tests to validate your infrastructure code before deployment.
Conclusion
By leveraging GitLab CI/CD and Terraform, you could automate the deployment and control of your infrastructure, main to greater efficient and reliable operations. This approach no longer saves time but also reduces the hazard of human mistakes. Experiment with exclusive configurations and amplify the pipeline to fulfill your specific wishes. Happy automating!