Threat detection and incident response are critical components of any organization’s security strategy, and AWS provides a range of tools and services to help with these tasks.
On AWS , threat detection typically involves monitoring for unusual activity and potential security threats across your AWS accounts and resources. This can include monitoring network traffic, access logs, and API activity for signs of unauthorized access, data exfiltration, or other suspicious activity.
Process to Implement security incident response
Organizations must have well-defined security incident response procedures in place to ensure a prompt and effective response to security incidents. These procedures should include clear roles and responsibilities, escalation paths, and communication channels.
Step 1 : Preparation
Develop an incident response plan that outlines the roles and responsibilities of the incident response team, escalation paths, and communication channels. Ensure that all team members are trained and equipped to respond to security incidents. Regularly test the incident response plan to ensure its effectiveness.
Step 2: Identification
Detect and identify security incidents by monitoring network and system logs, alerts from security tools, and reports from users. Use automated tools, such as AWS GuardDuty, to detect anomalies and potential threats.
Step 3: Containment
Contain the incident to prevent further damage by isolating affected systems, blocking network traffic, or disabling compromised accounts. Follow established procedures to preserve evidence and prevent data loss.
Step 4: Analysis
Analyze the incident to determine its scope, severity, and cause. Gather information from various sources, including logs, network traffic, and system images. Use AWS services, such as Amazon CloudWatch, AWS Config, and AWS CloudTrail, to gather relevant data.
Step 5: Eradication
Remove the cause of the incident by removing malware, patching vulnerabilities, or restoring affected systems from backups. Ensure that all affected systems are thoroughly scanned and cleaned before returning them to service.
Step 6: Recovery
Restore normal business operations by verifying the integrity of restored systems and data. Monitor systems and logs for any signs of re-infection or further incidents.
Step 7: Documentation
Conduct a post-incident review to identify areas for improvement in the incident response plan and procedures. Document lessons learned and use them to update the incident response plan and improve security posture.
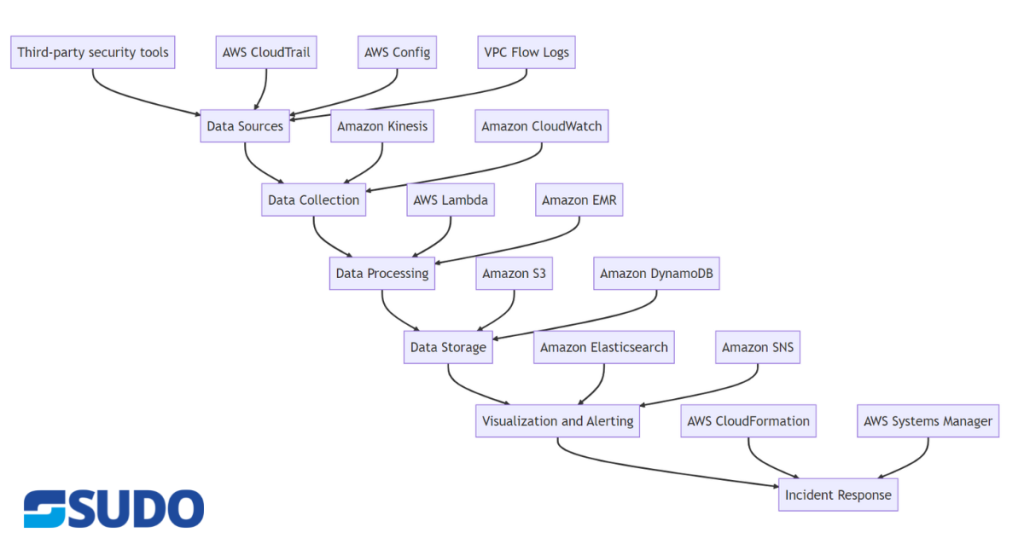
Architecture
The architecture for threat detection and incident response on AWS typically involves the following components:
- Data Sources: These include various AWS services like AWS CloudTrail, AWS Config, VPC Flow Logs, and third-party security tools that generate logs and other security-related data.
- Data Collection: AWS services like Amazon Kinesis and Amazon CloudWatch can collect data from various sources in real-time.
- Data Processing: AWS services like AWS Lambda and Amazon EMR can process data in real-time, analyze it, and identify potential security threats.
- Data Storage: AWS services like Amazon S3 and Amazon DynamoDB can store the data generated from various sources.
- Visualization and Alerting: AWS services like Amazon Elasticsearch and Amazon SNS can visualize the processed data, generate alerts for potential security threats, and notify relevant stakeholders.
- Incident Response: AWS services like AWS CloudFormation and AWS Systems Manager can automate the incident response process and take corrective actions based on pre-defined response playbooks.
The data flow in this architecture involves the continuous collection, processing, and analysis of security-related data from various sources, with the goal of identifying and responding to potential security threats in real-time.
Tools
AWS provides a range of tools and services to help with threat detection in your AWS environment. Some of the best tools for threat detection on AWS include:
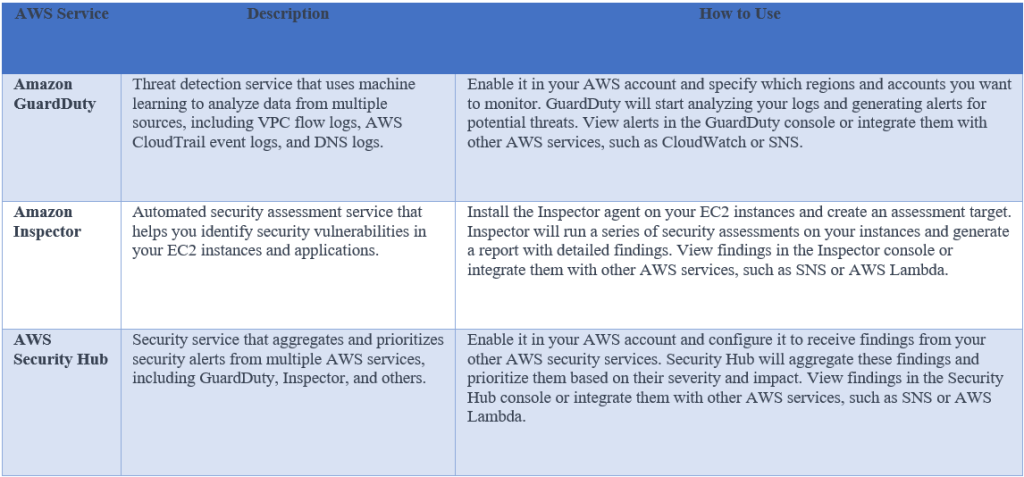
1. Amazon GuardDuty: A threat detection service that continuously monitors your AWS accounts for unusual activity and potential security threats. It uses machine learning and anomaly detection to analyze log data from VPC Flow Logs, AWS CloudTrail, and DNS logs to detect threats such as cryptojacking, reconnaissance and privilege escalation.
2. Amazon Inspector: An automated security assessment service that helps you identify security vulnerabilities in your applications and infrastructure. It analyzes your resources for security issues, such as missing patches or misconfigurations, and provides detailed findings and remediation guidance.
3. AWS Security Hub: A centralized dashboard that aggregates security findings from multiple AWS services, including Inspector, GuardDuty, and Amazon Macie. It provides a comprehensive view of your security posture, with prioritized findings and automated remediation workflows.
4. AWS Config: It is a configuration management service that provides a detailed inventory of your AWS resources and their configurations. It can be used to monitor for changes to your resources that could impact security, such as changes to security group rules or IAM policies.
5. AWS CloudTrail: It is an aws service that logs all API activity in your AWS accounts. It can be used to detect unauthorized activity, such as attempts to modify security groups or create new IAM users.
6. VPC Flow Logs: A feature that captures information about the IP traffic going to and from network interfaces in your VPC. It can be used to monitor for unusual network traffic, such as large volumes of outbound traffic to suspicious IP addresses.
Best Practices
Implementing threat detection and incident response on AWS requires a multi-layered approach that involves leveraging various AWS services and implementing security best practices. Here is a list of best practices for implementing threat detection and incident response on AWS:
Conducting a threat assessment
It is essential to conduct a thorough threat assessment to identify potential threats and vulnerabilities before you implement any security measures. This should include

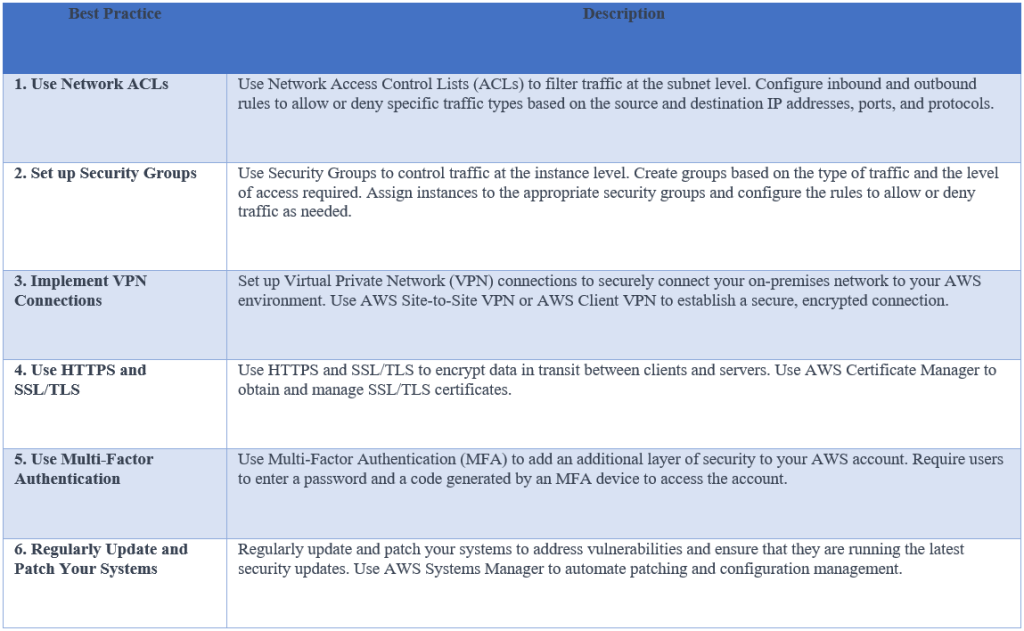
Implementing network security best practices
AWS provides a range of network security features that can be used to enhance security. These include using network ACLs, setting up security groups, and implementing VPN connections.
Here are some best practices that you can implement to secure your network on AWS:
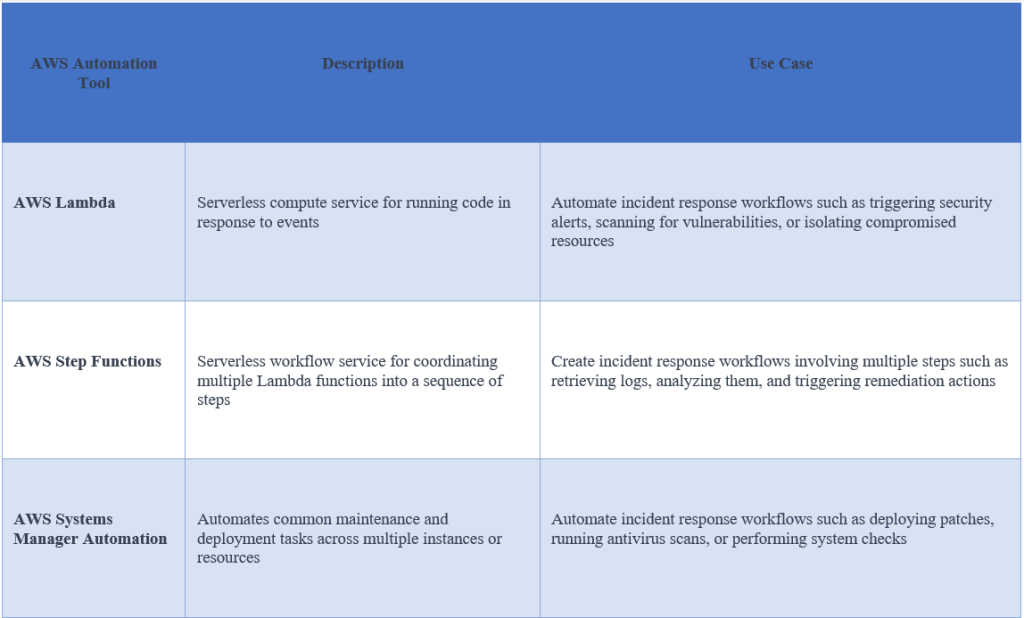
Using automation for incident response
AWS is providing a range of automation tools that can be used to respond to security incidents quickly and efficiently. These include AWS Lambda, AWS Step Functions, and AWS Systems Manager Automation. These tools can be used to automate incident response workflows, such as isolating compromised resources and triggering security alerts.
Here are some examples of how you can use these tools for incident response:
Using AWS services for threat detection
AWS provides several services that can be used to detect potential threats, including Amazon GuardDuty, Amazon Inspector, and AWS Security Hub. These services can help identify potential security risks and provide insights into security posture.
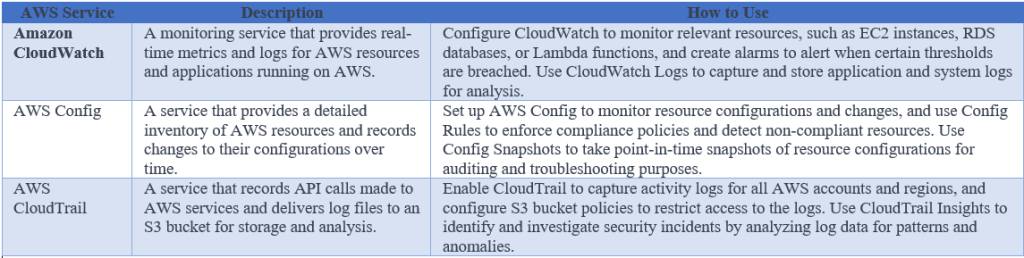
Implementing security monitoring
This tool is used for security monitoring, including Amazon CloudWatch, AWS Config, and AWS CloudTrail. These services can be used to monitor activity on the network, detect anomalies, and collect logs for further analysis.
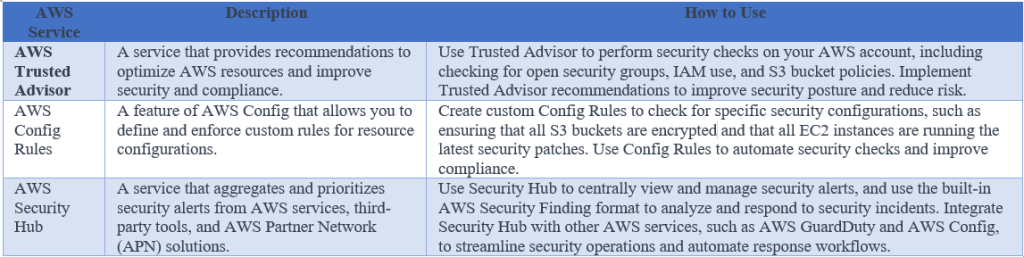
Conducting regular security audits
Regular security audits surely help identify potential vulnerabilities and ensure that security measures are being implemented effectively. AWS provides several tools that can be used to conduct security audits, including AWS Trusted Advisor, AWS Config Rules and AWS Security Hub.
Conclusion
The architecture and dataflow for threat detection and incident response on AWS are designed to provide a comprehensive and automated approach to security, enabling organizations to quickly detect and respond to potential security threats. Here you can find effective threat detection and incident response procedures that are crucial for maintaining the security of your AWS infrastructure. By conducting regular security audits, implementing network security best practices, and using AWS services such as CloudTrail, Config, and CloudWatch, you can monitor your infrastructure and detect potential security threats in real-time. By having a well-defined incident response plan in place and utilizing AWS services like CloudFormation and Systems Manager, you can respond to security incidents promptly and effectively.