AWS data mesh is a way to collect and process data. A data mesh is a decentralized architectural pattern that enables organizations to securely and efficiently sharing data across teams – think micro services for data. AWS can help you to simplify your data management process and make it more efficient. AWS data mesh is […]
Optimized loading or importing of Data If your database does not have automated backups enabled, you can still take regular snapshots of your entire database. For this purpose, Set the backup retention period to a positive nonzero value. Once you do so, you can create an automatic backup by taking your database offline. A backup […]
The AWS Well-Architected Framework is a set of guidelines and best practices for building secure and scalable systems in the cloud. The framework consists of six pillars: In this blog post, we will take a closer look at each of the AWS Well-Architected Framework pillars. Security The first pillar of the AWS Well-Architected Framework is […]
How to backup Mysql Databases on Amazon RDS Cloud-based services let you scale capacity as your workload grows and automate the task of operating and maintaining your infrastructure at a lower cost. There are several best approaches to backup Mysql databases on Amazon RDS . Backing up data can be challenging, and the number of […]
Amazon EKS clusters are a managed Kubernetes service that makes it easy for you to deploy and manage containerized applications on AWS. Amazon EKS runs the Kubernetes management infrastructure for you across multiple AWS Availability Zones to eliminate a single point of failure. Amazon EKS is also integrated with many AWS services to provide robust […]
How to grow your business with Data Mesh and Data Lake on AWS What is Data Mesh? We define a data mesh as an infrastructure allowing different data consumers to share, consume, and collaborate on the same data without directly accessing or storing it. A data mesh consists of two primary components: a data discovery […]
How to monitor DataBricks with Amazon CloudWatch Importance of Monitoring Systems Software engineers often forget the importance of monitoring systems that run their infrastructure. When things go wrong, they do not have the tools to detect and react to issues fast enough. This can be dangerous because it may take them hours or even days […]
Load Balancing is often associated with a web server where multiple web servers must work together to host a website. To help ensure this, there are some critical aspects of load balancing that are essential. These tasks include: managing traffic spikes and preventing the network load from overtaking one server, minimizing the client request response […]
AWS Lambda is a compute service that lets you run code without provisioning or managing servers. Lambda automatically scales your application by running code in response to each trigger. Your code runs in parallel and processes each trigger individually, scaling precisely with the size of your workloads. Even if you process a million events per […]
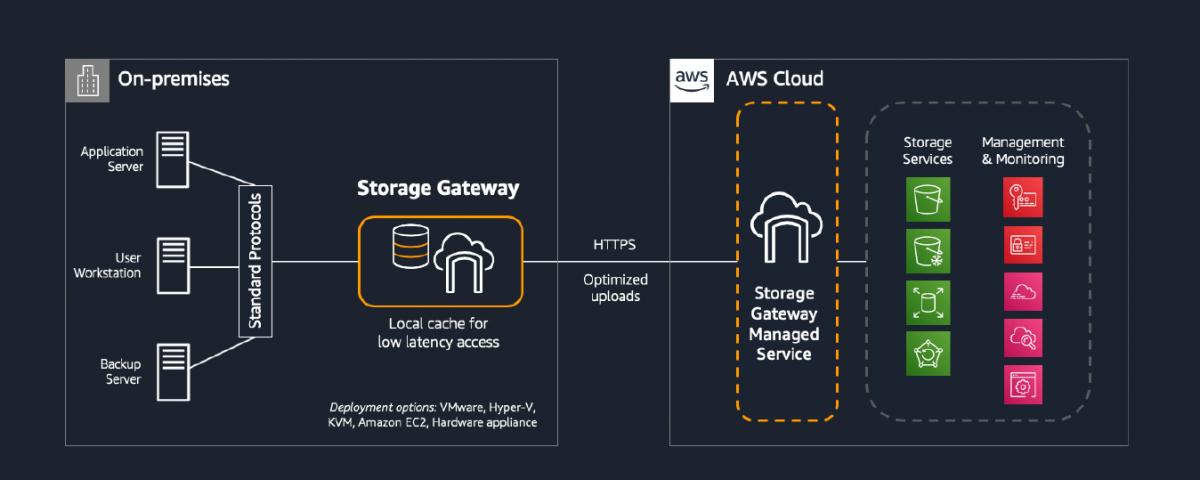
AWS Storage Gateway is a cloud storage gateway that connects an on-premises software appliance with cloud-based storage to provide seamless and secure integration between an organisation’s data and the AWS storage infrastructure. The Storage Gateway appliance is deployed as a virtual machine (VM) on a host in the customer’s data centre. The appliance connects to […]

![What is AWS data mesh and why its amazing [5 min read]](https://sudoconsultants.com/wp-content/uploads/2022/11/Data-Mesh.png)

![The Essential 6 Pillars of the AWS Well-Architected Framework [8 min Read]](https://sudoconsultants.com/wp-content/uploads/2022/11/AWS-Well-Architected-Framework.png)

![Easy Read – Amazon EKS Clusters [4 min]](https://sudoconsultants.com/wp-content/uploads/2022/10/Amazon-EKS-Clusters-sudo.png)