When Careem was acquired by Uber for $3.1 billion in 2019, it became the Middle East’s first unicorn. Careem, was the pioneer in the region’s ride-hailing economy, and has expanded its services as an everyday super app to include: mass transportation, delivery, and payments. However, its size and popularity, with over 50 million users, have […]
In this article you will learn how to setup Amazon Web Services (AWS) Web Application Firewall (WAF) to protect your business data from web scrapers and other malicious traffic. Our step-by-step guide covers the creation of AWS WAF instance, adding security rules and rule groups, and configuring metrics to monitor performance and identify potential threats. […]
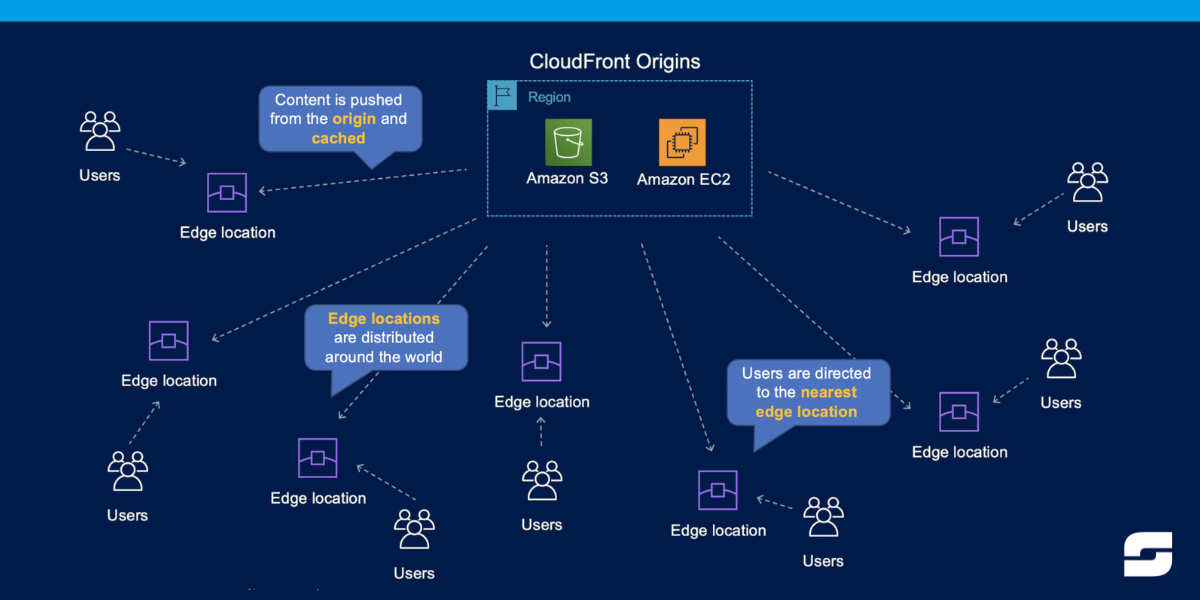
Cloudfront is a content delivery network (CDN) provided by Amazon Web Services (AWS). It is used to distribute web content globally to end-users with low latency, high data transfer speeds, and high availability. In this post, we will dive deep into the world of AWS Cloudfront and explore its key features, benefits, and use cases. […]
In the previous article, we discussed the importance of securing AWS Lambda and a few steps involved in implementing security and compliance considerations. To build upon this foundation, in this article, we will dive deeper into the remaining security and compliance considerations when using AWS Lambda. These considerations will help ensure the protection of your […]
AWS Lambda is a serverless computing service that enables you to run code without provisioning or managing servers. As with any other service, there are security and compliance considerations that you should take into account when using Lambda. Some key security and compliance considerations when using Lambda include: When setting up security and compliance considerations […]
AWS Fargate is a fully managed service for running containers on Amazon Web Services (AWS). It provides a way to run containerized applications without having to manage the underlying infrastructure. In this blog post, we will explore what AWS Fargate is, how it works, the advantages of using it, and real-world case studies of businesses […]
A serverless data warehouse is a type of data warehouse that does not require the user to provision, scale, or manage servers. Instead, the user only pays for the amount of storage and computational resources they use, and the provider is responsible for managing and scaling the infrastructure. The most popular serverless data warehouse services […]
Building a serverless data warehouse on AWS can be done by using a combination of AWS services, including AWS Glue for data extraction, transformation, and loading (ETL); Amazon S3 for data storage; and Amazon Redshift Spectrum or Amazon Athena for data querying. Step 1 : Firstly, set up an Amazon S3 bucket to store the […]
Amazon API Gateway is a fully managed service that makes it easy for developers to create, publish, maintain, monitor, and secure APIs at any scale. With Amazon API Gateway; you can create RESTful, HTTP, and WebSocket APIs, which can be used to connect to various backends, including AWS Lambda, Amazon Elastic Container Service (ECS), and […]
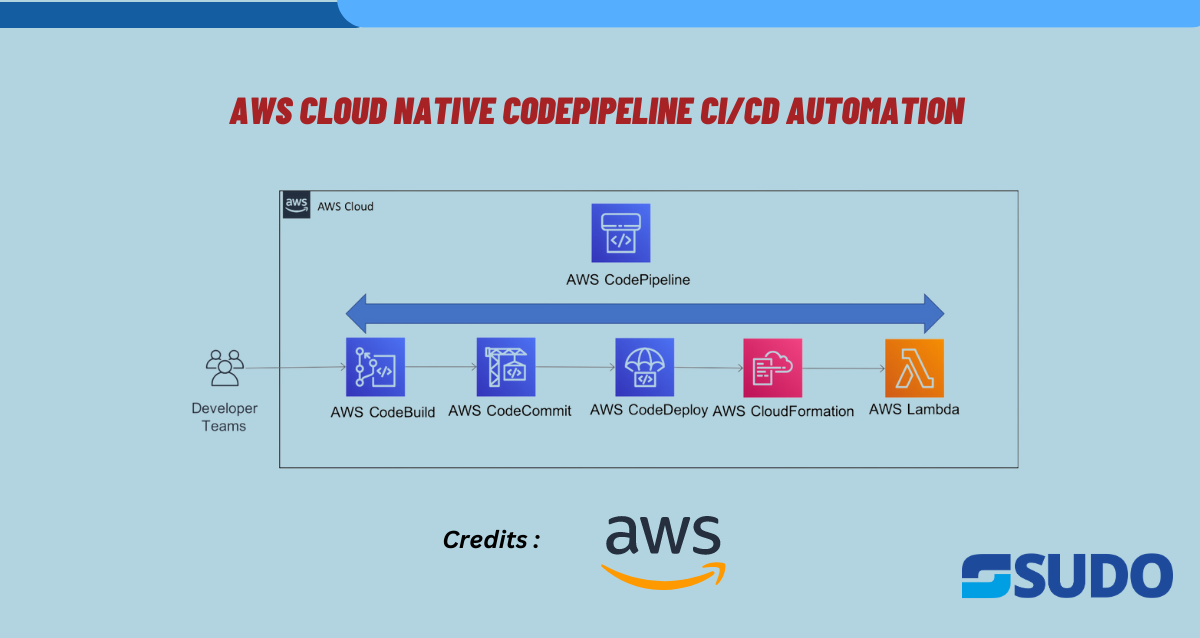
CI and CD stand for continuous integration and continuous delivery/continuous deployment. In other words, CI is a contemporary method of software development where incremental code changes are reliably and regularly produced. Code updates that are merged into the repository are made reliable by automated build-and-test procedures that are sparked by CI. Then, the code is […]

![Middle East Tech Giant | How Careem X AWS combat fraud [5 min Read]](https://sudoconsultants.com/wp-content/uploads/2023/02/Careem-x-aws.png)


![What is AWS Fargate and how businesses use it to lower infrastructure costs [6 Mins]](https://sudoconsultants.com/wp-content/uploads/2023/01/AWS-Fargate-sudo-consulatants.png)