
When Careem was acquired by Uber for $3.1 billion in 2019, it became the Middle East’s first unicorn.
Careem, was the pioneer in the region’s ride-hailing economy, and has expanded its services as an everyday super app to include: mass transportation, delivery, and payments.
However, its size and popularity, with over 50 million users, have made it a prime target for fraudsters who are constantly looking for new loopholes to exploit and new ways to hijack legitimate accounts.
Let’s take a look Careem’s journey to build a fraud detection system that covers all of its services, including food deliveries, grocery deliveries, P2P transactions, and payments.

Crazy Wall
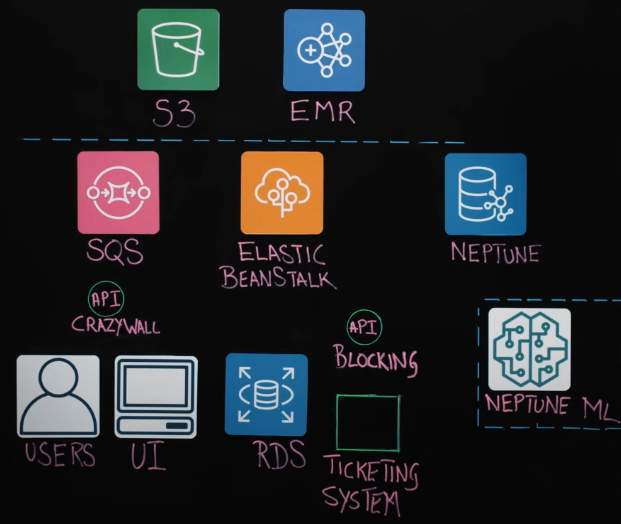
Careem’s fraud detection system, known as “Crazy Wall,” was built with the intention of having a blanket approach to cover all different types of fraud.
One of the most common frauds they faced was users gaining access to stolen credit card details and using them to make purchases on their platform.
To tackle this issue, Careem decided to implement a graph database, using AWS Neptune, to represent the identity of all their users and their data points. The data is populated with historical data and is updated in real-time as events occur on the app.
Pi Event Processor
The project uses a system called Pi Event Processor, which processes every event that users perform on the app, streams it in real-time to a core code base, and is transformed and written to the database.
The data is then extracted and used to run a simple set of rules to decide whether the action performed by the user is likely to be fraudulent or not. The project has already achieved a precision of 90%.
Careem has also exposed their graph to an API, allowing any division within the company to query the graph and get details about a user and their identity in the graph. This has been used for downstream tasks, such as building machine learning models and creating a UI for viewing a particular user in the graph.
In terms of the future, the aim is to add more intelligence to the system, using machine learning (leveraging AWS Neptune ML), and make the decision-making process even more precise.
Conclusion
Careem has successfully implemented a comprehensive fraud detection system using a graph database, which has proven to be effective in detecting and blocking fraudulent activities. The system is scalable and has been used by various divisions within the company, showcasing the benefits of having a centralized database that can be accessed by all.
Firewalls are useful for preventing application-layer attacks and malware. They are extremely useful for detecting and combating rogue activity across your network. Using a firewall to secure our client’s infrastructure allows us to configure their network with specific policies that block or allow traffic.
Firewalls also provide enhanced security levels for vulnerable networks: when firewalls are in place, unauthorized users cannot access private networks. Firewalls will also protect networks from phishing attacks.
- Tags:
- Careem
- Cloud Computing
- Firewall
- UAE