Introduction In this article we will be learning how we can access our AWS EC2 instances with the help of AWS System Manager, eliminating the need of SSH keys. Security is a paramount concern, and best practices dictate keeping our applications private. Developers and administrators often need to connect to EC2 Instances for their tasks. […]
AWS CloudWatch is helpful for storing and retrieving logs for various AWS resources. It tells us what is really happening with our infrastructure in the form of logs, metrics, alarms, and dashboards. Sometimes, there is a need to perform some action if something occurs within a resource e.g. an error or warning log. For this […]
AWS IAM is a vital help that permits us to control admittance to AWS assets and resources. It enables users to create and manage various identities i.e., IAM users, groups, roles, and policies. One can enforce the principle of least privilege, ensuring that users and multiple services have only the necessary permissions to perform their […]
Introduction AWS Step Functions is a powerful serverless service that allows you to design and implement complex workflows using a structured language called Amazon States Language (ASL). In this article, we will explore the use cases and the process of designing intricate workflows using AWS Step Functions, with a specific focus on a real-world example: […]
SUDO Consultants Will Showcase Its Innovations at Gitex Global 2023. SUDO Consultants a leading name in cloud, DevOps and cybersecurity, is excited to announce its participation as an exhibitor at the highly anticipated Gitex Global 2023 event. As usual, industry leaders, tech enthusiasts, and global innovators will join this mega event at the Dubai World […]
A VPC endpoint facilitates secure, private connections to AWS services and VPC endpoint services using AWS PrivateLink. Amazon VPC instances can communicate with these services without needing public IP addresses, ensuring that data traffic remains within the Amazon network. These VPC endpoints are essentially virtual devices that are designed to be horizontally scalable, redundant, and […]
Blockchain technology is revolutionizing the way we conduct business by providing transparency, security, and immutability to data. AWS Managed Blockchain, a fully managed service from Amazon Web Services, makes it easy to create and manage blockchain networks. In this blog post, we will discuss how to set up and configure a blockchain network using AWS […]
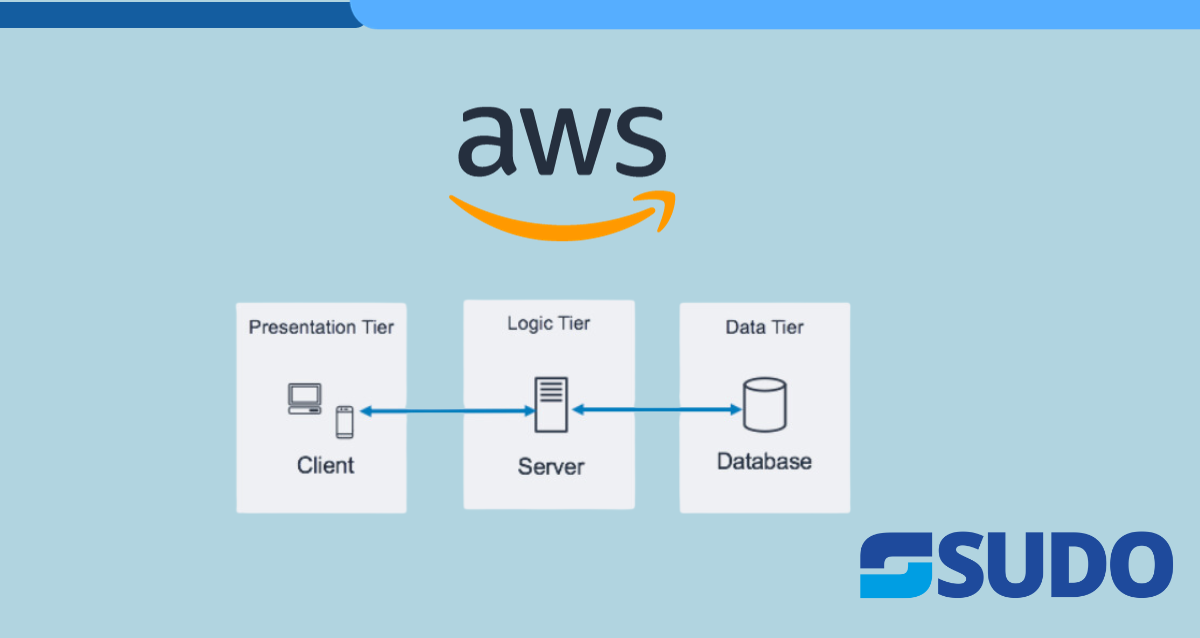
This blog post will comprise the necessary steps to design a 3-tier architecture in AWS. What is 3-Tier Architecture? The three-tier architecture stands as one of the predominant and widely adopted architectural paradigms in the software industry. It essentially revolves around the concept of dissecting our software application into three distinct and interconnected components, each […]
Introduction AWS Simple Storage Service (S3) offers robust data storage capabilities, and with cross-account replication, you can ensure data redundancy and disaster recovery by replicating objects from a source S3 bucket in one AWS account to a destination S3 bucket in another AWS account. This step-by-step guide will walk you through the process of setting […]
In today’s interconnected world, the security and privacy of your data are paramount. AWS PrivateLink offers a solution to securely access AWS services without traversing the public internet. By implementing PrivateLink, you can ensure data privacy and compliance while maintaining the benefits of AWS services. In this blog post, we will explain how to use […]