
By providing on-demand access to computing resources and cost-effective solutions, cloud computing has transformed the way businesses operate. It does, however, present challenges for cloud security.
Businesses must ensure that their data is secure and that only authorized personnel have access to their cloud resources.
Introduction
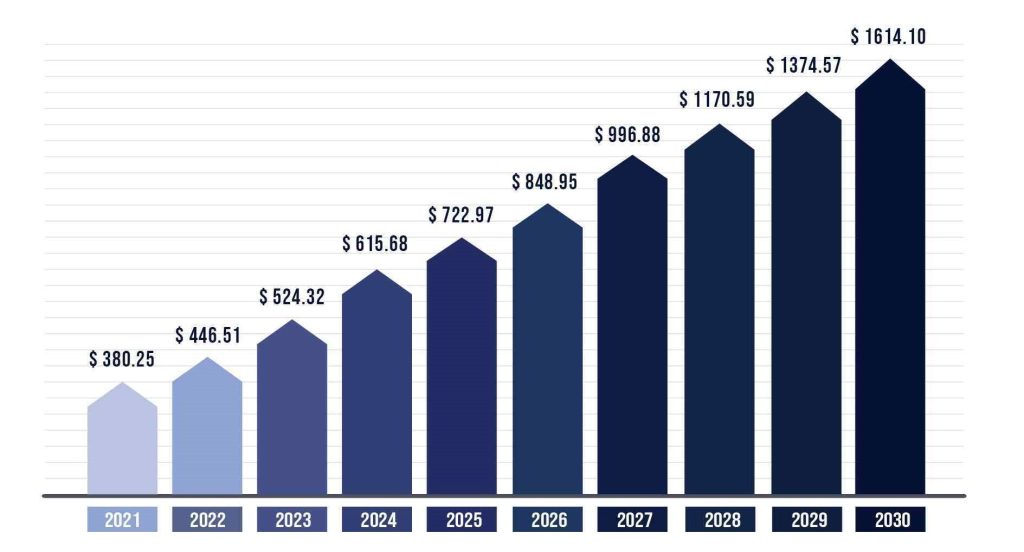
The use of cloud computing services has grown significantly in recent years. The global cloud computing market was valued at USD $484 billion in 2022 and is expected to expand at a compound annual growth rate (CAGR) of 14.1% from 2023 to 2030
While cloud service providers take precautions to secure their infrastructure, businesses must also take responsibility for the security of their data and applications. Failure to do so can have disastrous consequences, such as data breaches, lost customer trust, and financial loss.
See: 5 biggest data breaches, how they happened and what could have been done to prevent them.
In this article, we’ll look at the six most common cloud security mistakes to avoid:
1. Not Having a Clear Cloud Computing Strategy
When it comes to cloud computing, the first critical mistake businesses make is not having a clear strategy.
A cloud computing strategy should be in line with your overall business objectives and should detail how the cloud will be used to achieve those objectives.
Businesses risk wasting time, money, and resources on solutions that do not align with their goals or provide the desired benefits if they do not have a clear strategy.
2. Not Understanding the Shared Responsibility Model
In cloud security, the shared responsibility model is vital. It defines the relationship between the cloud service provider and the customer.
The provider is responsible for infrastructure security, while the customer(you) is responsible for data and application security.
You may mistakenly believe that the provider is responsible for all security measures if they do not understand this model. This is where Managed Cloud Services comes in. By leveraging the Cloud Experts, you ensure your infrastructure runs smoothly, customer data is secure and operational costs are minimal.
3. Failing to Encrypt Sensitive Data
Encryption is the process of converting data into a code that only authorized personnel can access.
Failure to encrypt sensitive cloud data not only exposes it to cybercriminals. Encryption can be a highly effective technique for achieving compliance requirements; GDPR (General Data Protection Regulation) for example.
Businesses MUST ensure that all sensitive data is encrypted during both transit and storage.
4. Weak Password Management
One of the most common causes of security breaches is weak passwords.
Employees may use the same password for multiple accounts, use passwords that are easily guessable, or fail to change their passwords on a regular basis.
Businesses must implement STRONG password policies, such as requiring password changes and utilizing multi-factor authentication. Also providing training for staff can greatly improve operational security.
5. Neglecting to Regularly Monitor and Update Security Protocols
To protect against emerging threats, security protocols must be monitored and updated on a regular basis.
Failure to update security protocols can expose businesses to new and evolving threats.
Regular monitoring of security protocols can aid in identifying flaws and correcting them before they are exploited.
6. Overlooking Compliance and Regulations
Another critical error that businesses make when it comes to cloud computing is failing to consider compliance and regulations.
Specific regulations and compliance requirements may apply depending on the industry and location. Failure to comply with these regulations can result in costly fines, legal issues, and reputational harm.

Conclusion | Cloud Security
The cloud has changed the way businesses operate. It does, however, present new challenges for security management. Businesses must ensure that their data is secure and that only authorized personnel have access to their cloud resources. Businesses can strengthen their cloud security posture and protect their valuable assets by avoiding the six common mistakes outlined in this article.