
Introduction
No matter what the size of an organization is, the security of its applications always stays a top priority concern. With the advancements made in major sectors, the number of cyber threats have also increased in number. Because of this the task of protecting user data and preventing the application from unauthorized access has become extremely crucial. This article typically focuses on application’s security with the usage of AWS Cognito User Pools which offers ideal solutions for enhancing the measures.
Importance of Application Security
Application security is basically a very broad subject to discuss because it involves things like practice of such technologies which are specifically used for the purpose of protecting application’s data from cyber threats. The data that needs protection might be a simple financial transaction or some personal information. If you are planning on delaying this security issue which needs your undivided attention then there could be financial losses along with legal consequences.
Introduction to AWS Cognito User Pools
Before getting any further, let us start with the introduction to AWS Cognito User Pools. It is basically an important component of Amazon Web Services (AWS). Its main aim is to provide solutions related to the management of user authentication and authorization both in mobile and web. It comes with a user directory that assists developers to add functionalities like sign-in, sign-up etc. to their applications. The best thing about this is that it doesn’t involve the need for complex authentication mechanisms.
Overview of What the Article Will Cover
This article is going to be about AWS Cognito User Pools and its functionalities that could help the organizations in the best possible way. We will provide a step-by-step guide on how to set up user pools, implement the authentication and authorization functionalities, secure the data, monitor the on-going activities, perform integration with other AWS services, and adopt the best possible practices for optimal security posture.
Moreover, we will also be discussing some real-world scenarios which will provide insights regarding the practical applications of AWS Cognito User Pools in taking extra security measures.
Setting Up User Pools with AWS CLI
For setting up the user pool using the AWS CLI approach, you can follow the below mentioned steps.
- If you haven’t installed or configured AWS CLI on your machine then do it as your first step.
- Open the command prompt.
- Create a new user pool by using the command “aws Cognito-idp”. Specify the settings such as pool name, password and MFA (Multi-Factor Authentication).
Example command
aws cognito-idp create-user-pool --pool-name MyUserPool --policies PasswordPolicy='{"MinimumLength":8,"RequireUppercase":true,"RequireLowercase":true,"RequireNumbers":true,"RequireSymbols":true}' --sms-authentication-message-type REQUIRED --sms-verification-message 'Your verification code is {####}'- Once you have successfully created the pool, you can make other configurations using CLI commands.
Setting Up User Pools with AWS Console
The administrators are fully allowed to use the AWS Management Console for setting up user pools and that too with a GUI – Graphical User Interface.
- Go to Amazon Cognito service present in the AWS Management Console.
- To view or create new user pools, select “Manage User Pools” option.
- Select “Create a User Pool”.
- Fill out the important fields regarding the pool such as name, password, multi-factor authentication etc.
- After you are done with all the settings, click “Create Pool” button.
Luckily, administrators can use both the approaches for customizing the user pool settings by meeting all the security requirements. No matter which option they choose; CLI or GUI.
Implementing Authentication and Authorization Mechanisms with AWS CLI
Configuring Authentication Methods
- To configure the authentication methods for the user pool, use the AWS CLI command “update-user-pool”.
Example Command
aws cognito-idp update-user-pool –user-pool-id <user-pool-id> --policies ‘{“PasswordPolicy”:{“MinimumLength”:8,”RequireUppercase”:true,”RequireLowercase”:true,”RequireNumbers”:true,”RequireSymbols”:true}}’- In case of social identity providers like Facebook, Google or Amazon, use “create-identity-provider” command to successfully add them into the user pool.
Setting Up Authorization Rules
- If you come across the need to define custom attributes for the users then use “add-custom-attributes” command.
- For creating groups within the pool use “create-group” command.
- To implement authorization rules use “create-resource-server” command.
- Use “create-identity-provider” to control the access based on user groups and attributes.
Implementing Authentication and Authorization Mechanisms with AWS Console
Configuring Authentication Methods
- Go to Amazon Cognito service.
- Select the user pool you want and then navigate to the “App Integration” tab.
- Enable the authentication for password and username and also configure the password policies.
- Go to “Identity Providers” tab to add social identity providers. Keep following the prompt to add providers.
Setting Up Authorization Rules
- Navigate to the “Attributes” tab to define custom attributes by staying within the user pool settings.
- Now create groups within the user pool by switching to “Groups” tab and assign users to these groups accordingly.
- In order to implement authorization rules select “Triggers” tab and configure Lambda triggers. This will enforce custom authorization logic based on group membership and user attributes.
Both the approaches are available for the administrators so that they can configure the authentication and authorization mechanisms within the user pools. In this way they will be able to control the access to resources based on attributes and identities.
Securing User Data with AWS CLI
Encryption at Rest and in Transit
- For enabling encryption at rest for user data in Cognito user pools, use “update-user-pool” command with AdminCreateUserConfig parameter set. This will surely enable encryption.
Example command
aws cognito-idp update-user-pool --user-pool-id <user-pool-id> --admin-create-user-config AllowAdminCreateUserOnly=true- To enforce encryption in transit, make sure that HTTPS is enabled for all the communication between client devices and AWS Cognito Service.
Implementing Fine-Grained Access Control Policies
- You can configure the fine-grained access control policies using AWS CLI commands.
- To define scopes and resources within the user pool use “create-resource-server” command.
- For setting up the permissions use “create-resource-server-policy” command. This will help in specifying which groups or users have access to scopes and resources.
Securing User Data with AWS Console
Encryption at Rest and in Transit
- Go to Amazon Cognito service using AWS Management Console.
- After selecting the desired user pool, go to “Security Configuration” tab.
- Configure the right settings under “Data Encryption” to enable encryption at rest.
- To encrypt data in transit make sure “HTTPS only” option is selected under the “App Client Settings”.
Implementing Fine-Grained Access Control Policies
- Stay within the user pool settings and head towards “Resource Servers” tab.
- You will need to define the resource servers and scopes in order to represent the user data and permissions within the pool.
- Under the “Resource Server Policies” section, configure the access control policies. You can perform the required configurations by specifying which groups or users have access to specific scopes and resources.
By following these steps properly, administrators can make sure that the user data in the user pools remain secure by enabling encryption at rest and in transit. Along with this, fine-grained access control policies also restrict the access to sensitive data.
Monitoring and Logging Activities with AWS CLI
Integration with AWS CloudWatch
- You can use AWS CLI commands to enable integration between AWS CloudWatch and AWS Cognito User Pool.
- CloudWatch integration is beneficial for monitoring user authentication activities. For this, run “update-user-pool” command with AdminCreateUserConfig parameter set.
Example command
aws cognito-idp update-user-pool --user-pool-id <user-pool-id> --admin-create-user-config CloudWatchLogsRoleArn=<cloudwatch-role-arn>Add Amazon Resource Name (ARN) of the IAM role which gives permissions for CloudWatch logging and replace <cloudwatch-role-arn> with it.
Setting Up Alerts for Suspicious Behavior
- For detecting anomalies in user authentication activities, you need to create metric filters and alarms using CloudWatch Console or AWS CLI commands.
- Start configuring the metric filters to identify events in the logs like failed login attempt etc.
- If you want to get notified as soon as predefined conditions are met then you can create CloudWatch alarms for this purpose.
Monitoring and Logging Activities with AWS Console
Integration with AWS CloudWatch
- Go to Amazon Cognito service.
- Select the user pool of your choice and switch to “General Settings” tab.
- Look for the “Monitoring” section. From there enable CloudWatch Logs and also specify the IAM role that allows for CloudWatch logging.
Setting Up Alerts for Suspicious Behavior
- Go to CloudWatch service console and head towards “Logs” section. Find the group that is associated with the Cognito user pool.
- Now it is time to define the metric filters to extract information from the logs and identify patterns for suspicious behavior.
- Creating CloudWatch alarms based on metric filters will either trigger the automated responses or notify the administrators whenever suspicious activities are detected.
- Using AWS CLI commands along with AWS Management Console will allow the administrators to authenticate the activities, set up alarms or notifications in case of suspicious behavior and detect anomalies. This will surely enhance the security of the application.
Integrating with Other AWS Services with AWS CLI
Integration with AWS Lambda
- To implement custom authentication flows create and configure the Lambda functions by using AWS CLI commands.
- Use “create-function” command to create the Lambda function.
- Now configure the AWS Cognito User Pool to trigger the Lambda functions using “update-user-pool” command.
Example command
aws lambda create-function --function-name MyAuthenticationFunction --runtime nodejs14.x --handler index.handler --role <lambda-role-arn> --code S3Bucket=<bucket-name>,S3Key=<object-key>
aws cognito-idp update-user-pool --user-pool-id <user-pool-id> --lambda-config PreSignUp=<lambda-function-arn>Replace all the values present in angle brackets “< >” with appropriate values.
Integration with Amazon API Gateway
- Secure APIs by creating and configuring Amazon API Gateway with the help of JWT tokens or OAuth 2.0.
- To create a REST API in Amazon API Gateway use “create-rest-api” command.
- For using AWS Cognito User Pools for authorization and authentication purpose, configure the authorizers in API Gateway.
Example command
aws apigateway create-rest-api --name MyAPI
aws apigateway create-authorizer --rest-api-id <rest-api-id> --name MyAuthorizer --type COGNITO_USER_POOLS --provider-arns <user-pool-arn>Replace <user-pool-arn> and <rest-api-id> with appropriate values.
Integrating with Other AWS Services with AWS Management Console
Integration with AWS Lambda
- Go to AWS Lambda service.
- Use “Create Function” button to create a Lambda function. Configure it to handle the authentication logic.
- Now navigate to AWS Cognito Service, select user pool and head towards the “Triggers” tab to associate the Lambda function with authentication triggers.
Integration with Amazon API Gateway
- Go to Amazon API Gateway service.
- Create a REST API and configure it.
- To use AWS Cognito User Pools for authorization and authentication, configure the authorizers in API Gateway.
Adhering to Best Practices
Keep this thing in mind that during the setup and configuration process, adhere to the best practices to ensure optimal security performance.
- Keep all the dependencies and components updated.
- To minimize the risk of unauthorized access, make sure to implement frequent rotation of tokens, access keys and credentials.
- Access and audit the security configurations of AWS Cognito User Pools along with their associated services to resolve possible security threats.
Real-World Case Studies and Examples
Scenario 1:
A mobile application uses AWS Cognito User Pools for user authorization and authentication which ensures that only the associated users access sensitive financial data through fine-grained access control and MFA.
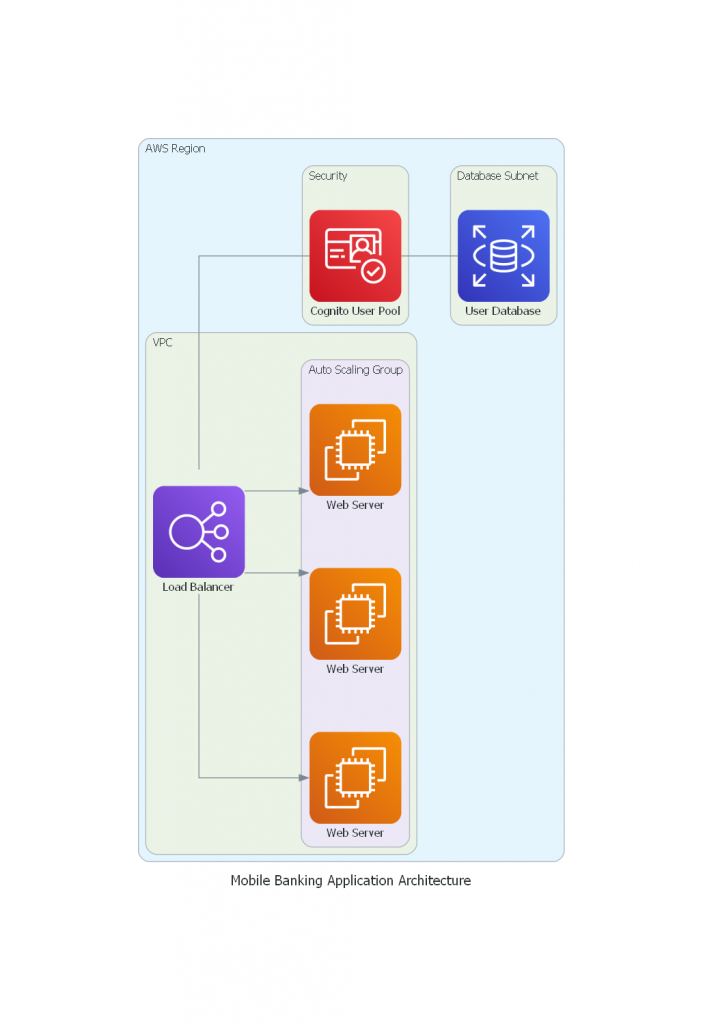
Scenario 2:
An E-commerce platform integrates Amazon DynamoDB with AWS Cognito User Pools to store user data. Role-based access control is also implemented which ensures that only the employees who are authorized can modify the data.
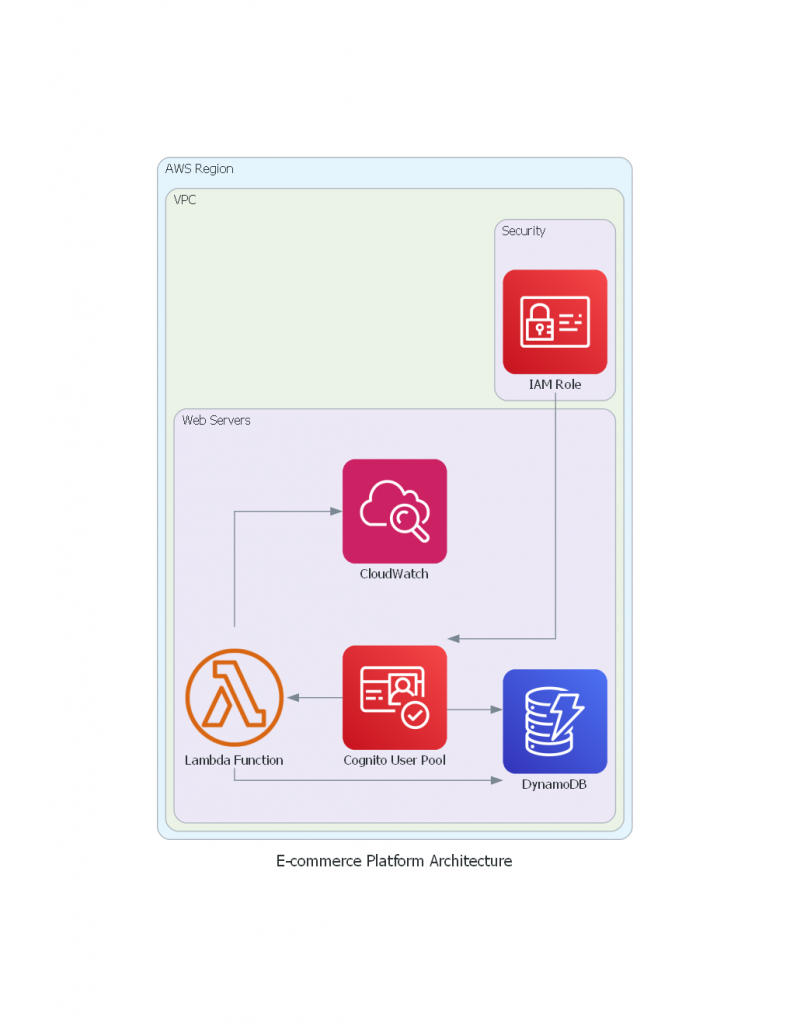
Conclusion
All in all, AWS Cognito User Pools provide robust solutions for the management of user identities and access control in applications. By following the steps mentioned in this guide and adhering to the best practices, the organizations can fully use the AWS Cognito User Pools to protect the data from unauthorized access.