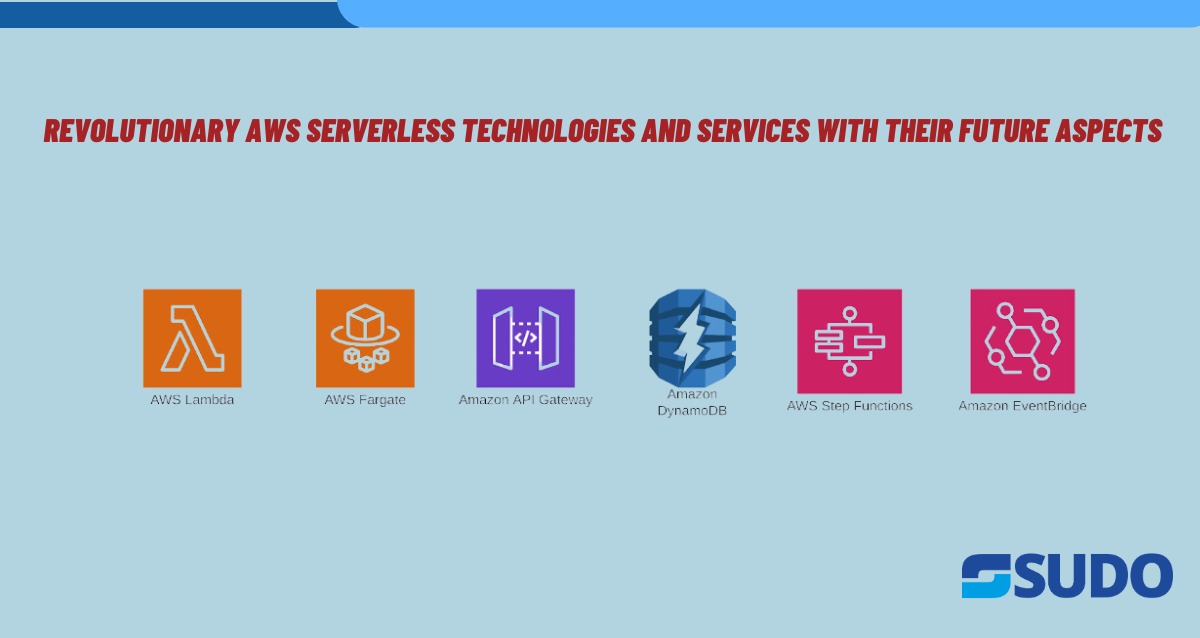
Introduction In this article, we will delve deep into the world of Amazon FSx for Lustre and explore how it can transform your data processing capabilities. We will begin by understanding the concept of data bottlenecks in big data processing and their impact on organizations. Then, we will introduce Amazon FSx for Lustre as a […]
Let’s explore the ins and outs of IT support services including Cloud Migration, DevOps and Cybersecurity – There is a wealth of resources available to businesses and individuals alike. So grab a cup of your favorite coffee, and let’s dive headfirst into the world of IT support in Dubai! The Importance of IT Support in […]
Cloud computing has transformed the IT industry drastically by providing on-demand access to computing resources such as servers, storage, databases, and software applications over the internet. This has drastically reduced the time and cost involved in setting up and maintaining an IT infrastructure. Previously, organizations had to invest a significant amount of money and time […]
Moving to a top cloud platform like AWS can be an excellent solution for websites that require high performance and uptime. You gain access to advanced features such as high availability, automated scalability, and replication across globally distributed data centers by utilizing cloud platforms. These features can assist you in achieving optimal website performance and uptime, […]
More and more countries around the world are putting in place strict data privacy laws that apply internationally. As a result, the number of countries that provide a GDPR-free shelters is decreasing. Executives in charge of data privacy and security at companies that do business all over the world MUST use a cross-regulatory compliance strategy […]
In this article we are going to discuss the services and components invloved in AWS Security Automation. These components are designed to work together to provide a comprehensive and automated approach to securing AWS resources and applications. By using these tools organizations one can not only reduce the risk of security breaches but also streamline […]
What is Infrastructure as Code (IaC)? Infrastructure as Code (IaC) , a practice of using code to manage and automate IT infrastructure, including servers, networks, storage, and other components. It involves defining infrastructure configurations as code, which can be version-controlled, tested, and deployed in a repeatable and consistent manner. Benefits of IaC There are several […]
Amazon Elastic Compute Cloud Instance, also known as an EC2 Instance, is a cloud computing service that provides resizable compute capacity in the cloud. EC2 instance types refer to the various configurations of virtual server instances that are available on the Amazon Web Services (AWS) platform. These instances are differentiated by the amount of: AWS […]
Threat detection and incident response are critical components of any organization’s security strategy, and AWS provides a range of tools and services to help with these tasks. On AWS , threat detection typically involves monitoring for unusual activity and potential security threats across your AWS accounts and resources. This can include monitoring network traffic, access […]
Nowadays, we are in a rapidly changing and evolving world wherein each moment a significant development is happening in a diverse direction of technology. These multi-directional changes create various opportunities to solve the challenges on the pathway toward excellence. Virtual Private Cloud(VPC) is an example of a modern-day solution to avoid many other overhead problems. […]