Docker has revolutionized the IT industry by stepping in 2013 as a platform that uses OS-level virtualization to expose software applications to the internet. By leveraging the containerization model, the earlier problems faced by development and operations teams have been mitigated. In the digital transformation era, we could see some formerly advanced methods and technologies […]
GISEC Global 2023, the Middle East’s largest and most influential cybersecurity event, presented an exciting lineup of features ranging from live cyber competitions to in-depth discussions on industry trends. As experts in the cybersecurity industry, we understand the importance of staying ahead of the curve in terms of threats and innovations. The overarching theme at […]
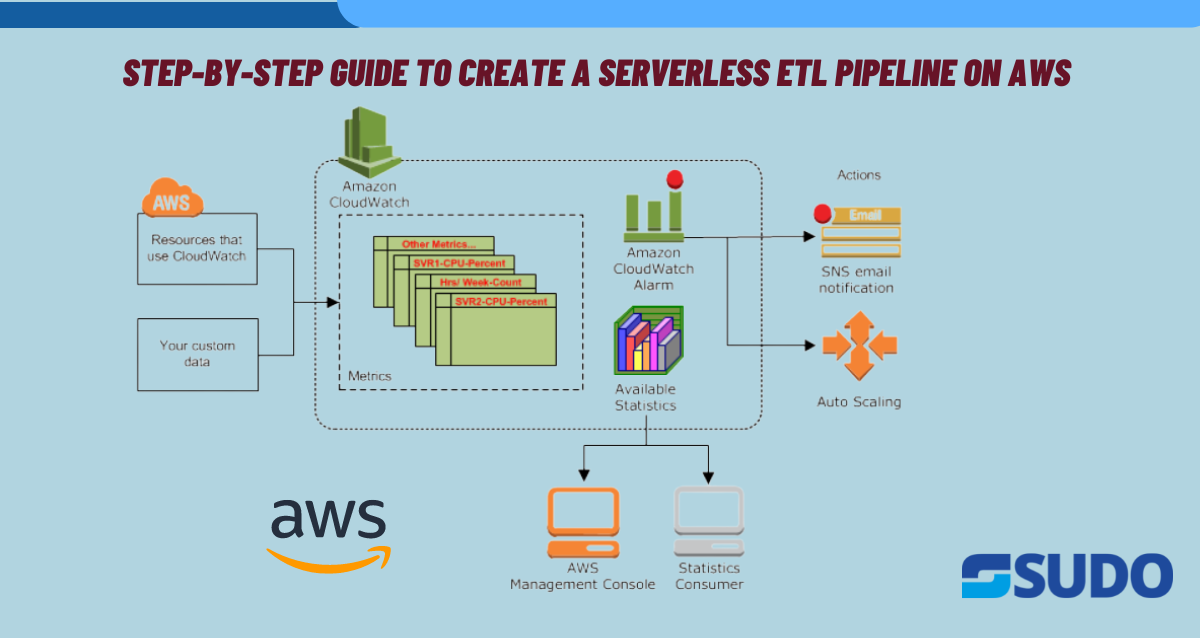
Why ETL Pipelines? Serverless ETL pipelines are becoming increasingly popular because they offer a number of benefits over traditional ETL pipelines. Here are some reasons why and for which projects ETL serverless pipelines are created: Use Cases ETL serverless pipelines can be used for a wide range of projects, including: Steps Creating a Serverless ETL […]
Why is AWS security important? AWS security is important for protecting an organization’s sensitive data, ensuring business continuity, complying with regulations, and mitigating security risks. It helps prevent financial losses, reputational damage, legal liabilities, and loss of customer trust. AWS security measures such as encryption, access controls, and monitoring can help prevent data breaches and […]
By providing on-demand access to computing resources and cost-effective solutions, cloud computing has transformed the way businesses operate. It does, however, present challenges for cloud security. Businesses must ensure that their data is secure and that only authorized personnel have access to their cloud resources. Introduction The use of cloud computing services has grown significantly […]
Introduction In today’s cloud-centric world, containerization has emerged as a groundbreaking paradigm, streamlining application deployment and scaling. While containers offer a myriad of advantages, managing their orchestration can often become challenging. Enter AWS Fargate, a pivotal service from Amazon Web Services (AWS), designed to alleviate this very challenge. Fargate revolutionizes container orchestration by allowing developers […]
The world is changing at a rapid speed like never before. Nowadays, there are many new ways of doing business, and technology has played a vital role. However, in the process of digital transformation, every practical domain faces a new challenge in each business case and the e-commerce industry. “If your business is not on […]
When Careem was acquired by Uber for $3.1 billion in 2019, it became the Middle East’s first unicorn. Careem, was the pioneer in the region’s ride-hailing economy, and has expanded its services as an everyday super app to include: mass transportation, delivery, and payments. However, its size and popularity, with over 50 million users, have […]
With the rise of cloud computing, monitoring has become an essential component of ensuring optimal cloud performance, availability, and security. Cloud monitoring tools are essential to helping organizations proactively identify and resolve issues that can affect their cloud systems and applications. In this post, we will share insights into cloud monitoring best practices and solutions […]
In this article you will learn how to setup Amazon Web Services (AWS) Web Application Firewall (WAF) to protect your business data from web scrapers and other malicious traffic. Our step-by-step guide covers the creation of AWS WAF instance, adding security rules and rule groups, and configuring metrics to monitor performance and identify potential threats. […]




![Middle East Tech Giant | How Careem X AWS combat fraud [5 min Read]](https://sudoconsultants.com/wp-content/uploads/2023/02/Careem-x-aws.png)